In this study, you will learn the simple tips for securing open SSH In Linux and how to configure them.
UNDERSTANDING THE SUBJECT MATTER
Following our previous studies on how to connect to a Linux server via SSH, and configuring & managing SSH, it is also imperative to learn some basic tips for securing open SSH in Linux.
Cyber criminals are aware of the default SSH configuration mechanism. They are out there with their sniffing tools trying to hack your system. It has happened to me before.
on one very good day that almost turned into a bad day, I logged in to one of the servers I was working on via SSH, and I saw thousands of attempted brute force attacks. About 20,000 password attempts failure if I remember correctly.
Securing SSH is very important especially if the server in question is internet facing. In this tutorial, I will show you some basic tips and their step by step process of how to secure SSH authentication in Linux.
Shall we?
Suggested Tutorial: Using Kickstart File In Linux With Examples
ACTION TIME
When I say use a muscular password, what I mean is that you use a very strong password. Do not use weak passwords or just one casual or easy to get passwords such as (password123, Password, redhat, Linux, Lisa, Jack, Victor, Oluwatomisin, etc). You can also make do with a password generator.
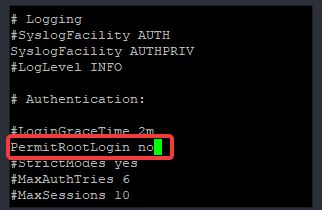
You can also deny SSH login for the root user. The root user is the superuser and can do and undo on the system. Disabling the root user makes the system less susceptible to attacks. This is one of the best practices in securing open SSH in Linux
Step By Step Process Of How To Disable root Login For SSH In Linux
a. Edit the SSH daemon configuration file.
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configlook for the parameter, “PermitRootLogin” and change the value to no.

b. Restart the sshd service
[root@DRDEV1 ~]# systemctl restart sshdsetting a password attempt limit for securing open SSH In Linux can be very effective. Anyone who tries to login with an incorrect password will be timed out after the set password limit.
Step By Step Process Of How To Set Password Attempt Limit For SSH In Linux
a. Edit the SSH daemon configuration file.
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configLook for the parameter MaxAuthTries and set the number of password attempt limit. In the screenshot below, the limit is set to 3 times.
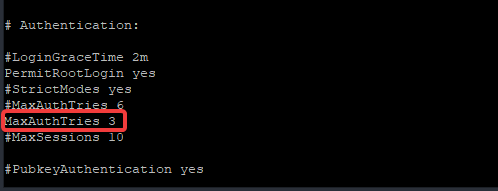
Note that this settings is different from locking a user account temporarily after failed login attempts which can be done in no.8 in this article
b. Restart the sshd service
[root@DRDEV1 ~]# systemctl restart sshdMake do with key-based authentication method instead of using the password authentication method. Passwords can be guessed while keys can’t. The Keys are generated by a mathematical algorithm in an encrypted format.
Click To See How To Generate & Configure SSH Key Based Authentication
Besides, using SSH keys means generating key pairs is a must. A Public key that will be on the target server(remote), and a private key that will be on the source server, and as the name implies, it’s your private key that will be on your server. Hence, no private keys, no authentication.
This method is very useful for securing SSH from both internal and external brute force attacks.
Step By Step Process Of How To Disable Password Authentication For SSH In Linux
a. Edit the SSH daemon configuration file.
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configlook for the parameter, “PasswordAuthentication” and change the value to no.
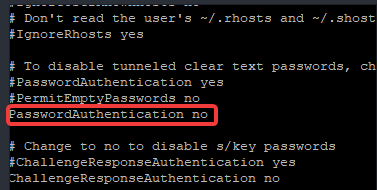
b. Restart the sshd service
[root@DRDEV1 ~]# systemctl restart sshdThe SSH default port is port 22 which is very susceptible to attacks.
It is recommended that this port is changed. However, this does not guaranty major protection because cyber criminals are fond of searching for back doors or loopholes which can be a result of a bad programming done on one of the services running on the system or the ports associated with those services.
SELinux is a very good security feature to counter this.
Click to see how you can configure & manage SELinux on your system.
More so, try not to use a casual port or an easy to get port such as 222, 2222, 11, etc). You can also use this link for a list of port numbers.
Step By Step Process Of How To Change SSH Port In Linux
a. Edit the SSH daemon configuration file.
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configlook for the parameter, “Port” and change the value to the new port or add the new port in the following line.
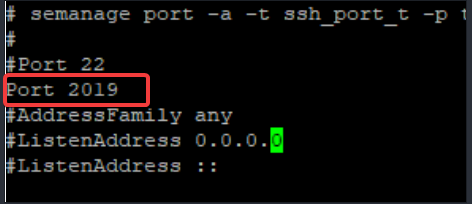
b. Restart the sshd service
[root@DRDEV1 ~]# systemctl restart sshdNB: relabel SSH type context, add the port to the firewall and restart the service if it doesn’t work
semanage port –a –t ssh_port_t –p tcp 2019firewall-cmd –add-port=2019/tcp –permanentsystemctl restart firewalld.servicesystemctl restart sshd.serviceSuggested Tutorial: Managing Services In Linux
You can limit user’s access to SSH by allowing some set of users, and/or only team members to login. You can add members to a group and configure SSH access for the group or groups only. See below step by step process of how to configure SSH access for a particular user or group.
Step By Step Process Of How To Limit User’s Access For SSH In Linux
a. Edit the SSH daemon configuration file.
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configAdd the parameter, (AllowGroups <group-name>) or (AllowUsers <username>)
If the group name, for example, is finance, add (AllowGroups finance), edit as shown below
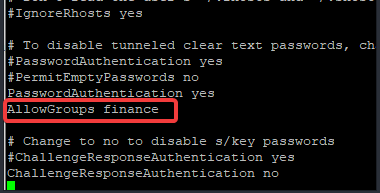
If the username or usernames are victor and oluwatomisin, edit as shown below
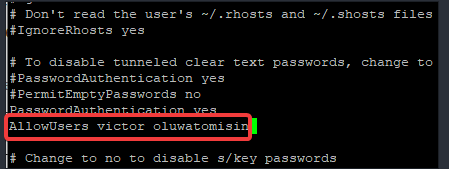
b. Restart the sshd service
[root@DRDEV1 ~]# systemctl restart sshdWhen an activity isn’t ongoing on your SSH terminal, the session will be timed out when you set idle time out. This is not only effective for external attacks, it is also effective for internal attacks, and can also save one from unintentional mistakes.
Step By Step Process Of How To Set Idle Time Out For SSH In Linux
a. Edit the SSH daemon configuration file.
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configAdd the line “ClientAliveInterval” as done below. The idle timeout is in seconds. If you want a timeout after 5 minutes, you will use 300.
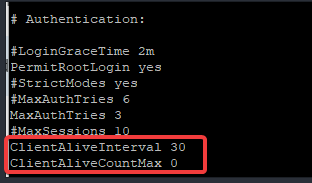
b. Restart the sshd service
[root@DRDEV1 ~]# systemctl restart sshdSuggested Tutorial: How To Properly Upgrade The Linux kernel
8. Lock User Accounts Temporarily After SSH Failed Login Attempts
The user account can be locked for a period of time after failed login attempts by using the pam_tally2 application or pam_faillock application. pam_tally2 or pam_faillock are part of Linux PAM (Pluggable Authentication Modules). The PAM package is shipped with most Linux distributions and has pam_tally2 and pam_faillock already installed.
Step By Step Process Of How To Temporarily Lock User Accounts After SSH Failed Login Attempts
a. Edit the SSH daemon configuration file
[root@DRDEV1 ~]# vi /etc/ssh/sshd_configlook for the parameter UsePAM and make sure the value is set to yes
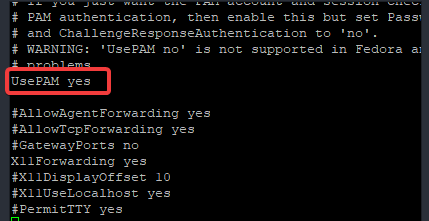
b. Configure PAM by following the steps in this link
There are many ways of securing open SSH in Linux. I have been able to give you a few simple tips to secure your SSH environment.
More so, it is important to inculcate the habit of enabling SELinux & firewall, especially if your server is internet facing.
Your feedback is welcomed. If you love others, you will share with others
Leave a Reply