
In this lesson, you will understand and configure how to lock user account in Linux after serveral failed login attempts.
UNDERSTANDING THE SUBJECT MATTER
Locking user’s account after numerous failed login attempts is one of the security measures you might want to put in place as an administrator.
In one of my lessons, I also talked about and demonstrated how one can secure a Linux system, especially, SSH, in various ways.
To be able to lock user accounts and keep track of failed login attempts, we can make use of PAM (Pluggable Authentication Module). PAM is basically used for authentication services. PAM can control authentication for systems, applications, services, etc. PAM has good security features.
There are a couple types of Linux PAMs we can use to lock user accounts. Some of them are;
*pam_tally
*pam_tally2
*pam_faillock
pam_tally and Pam_tally2 were majorly used in older versions of Linux systems and have now been replaced by pam_faillock in newer versions of Linux operating system. You can still use pam_tally2 if you wish to. However, we will be using the pam_faillock module in this lesson.
The pam_faillock module controls authentication of users for services such as login, SSH, su, con, at, cockpit, etc. which can be seen in the PAM configuration directory, just as shown below
[root@Tekneed pam.d]# cd /etc/pam.d/ ;ls -l
total 104
-rw-r--r--. 1 root root 272 Aug 12 2018 atd
-rw-r--r--. 1 root root 192 Sep 21 2019 chfn
-rw-r--r--. 1 root root 192 Sep 21 2019 chsh
-rw-r--r--. 1 root root 721 Sep 13 2019 cockpit
-rw-r--r--. 1 root root 232 Jul 14 08:54 config-util
-rw-r--r--. 1 root root 328 Jun 12 2019 crond
lrwxrwxrwx. 1 root root 32 Nov 14 01:33 fingerprint-auth -> /etc/authselect/fingerprint-auth
-rw-r--r--. 1 root root 715 Sep 21 2019 login
..........................
Let’s cat one of the files in the PAM configuration directory so that we can understand the syntax.
[root@Tekneed pam.d]# cat system-auth
# Generated by authselect on Mon Nov 14 01:33:27 2022
# Do not modify this file manually.
auth required pam_env.so
auth required pam_faildelay.so delay=2000000
....................................
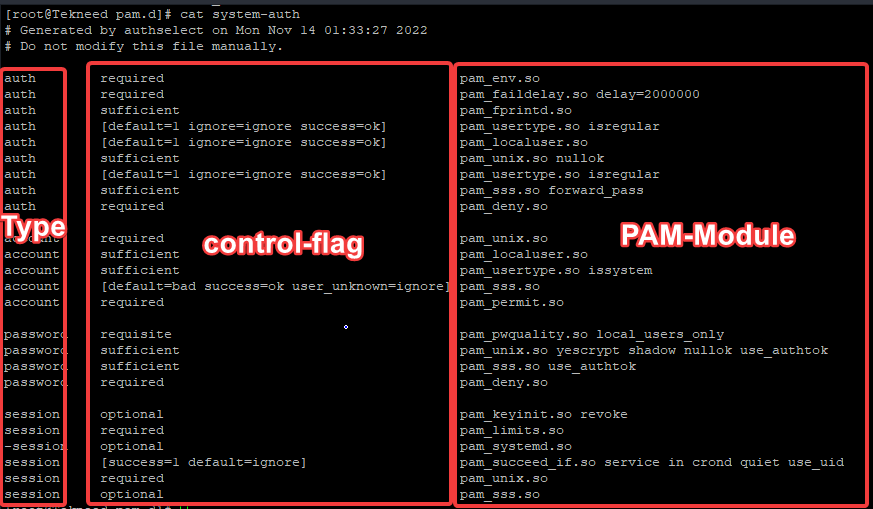
A PAM configuration file contains the following syntax.
Type control-flag PAM-Module <module-options>Type is the module interface with a specific service type, and there are four PAM service types. They are account, password, auth, and session.
*Account: Account is a PAM service type that manages account validation, i.e, verifies user accounts and validates that the user account is still active and not expired and can be allowed to login.
*Auth is a PAM service type that manages authentication services for accounts, i.e. it requests and validates that a user account password is correct.
*Password is a PAM service type that manages user accounts, i.e, it enforces password policies.
*Session is a PAM service type that manages user account sessions.
The second syntax is control-flag: The control-flag specifies the role of a PAM module in determining service access. Control-flag types are; binding, include, optional, required, requisite, sufficient, and substack.
Please click here to understand their effects.
The third syntax is the PAM-module: The PAM is the PAM module file name that will be responsible for doing the work. Sometimes, one may also add module options to the PAM just like we did in the ACTION TIME section below.
Having understood what PAM is and the syntax of a PAM configuration file, let’s see the step by step guide of how to lock user accounts in Linux after a certain number of failed login attempts in the Action Time section below.
ACTION TIME
The pam_faillock module comes in two parts, which are the pam_faillock.so and faillock.
The pam_faillock.so is the module while the faillock is a standalone program.
Below are the basic steps to take to lock a user account after n number of failed login attempts
*** Verify if faillock is loaded by PAM ***
[root@Tekneed ~]# rpm -ql pam |grep -i faillock
/usr/lib64/security/pam_faillock.so
/usr/sbin/faillock
/usr/share/doc/pam/txts/README.pam_faillock
/usr/share/man/man8/faillock.8.gz
/usr/share/man/man8/pam_faillock.8.gz
/var/run/faillock
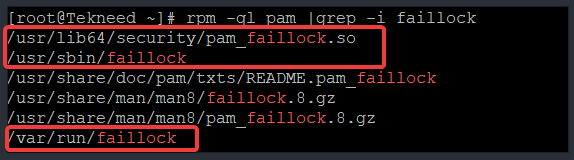
You can see that PAM rpm includes the pam_faillock.so module and the faillock binary command as highlighted above.
The /var/run/faillock directory is where the each user’s data file is located.
*** There are two important configuration files that needs to be changed which are ***
/etc/pam.d/system-auth, and
/etc/pam.d/password-auth
These configuration files can be edited manually which is not recommended or automatically by using tools such as authselect or authconfig which is recommended.
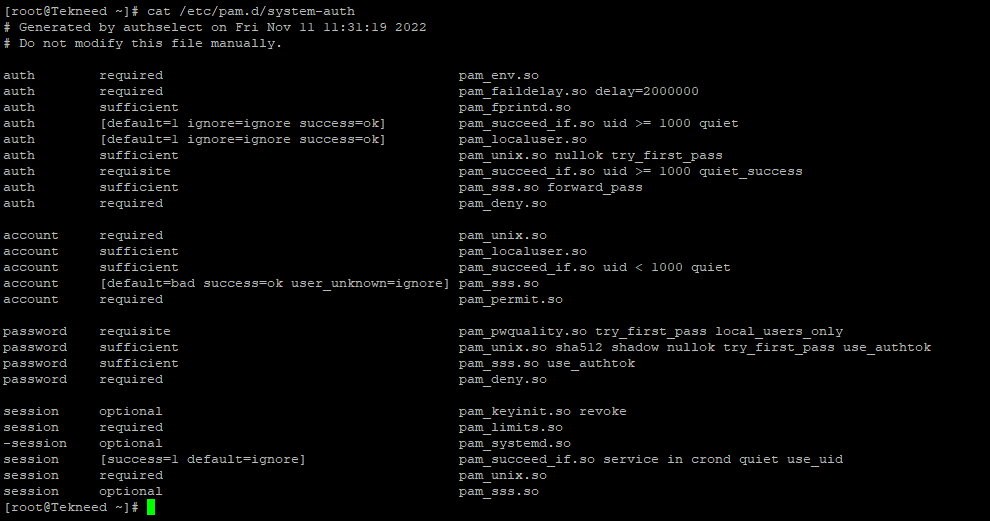
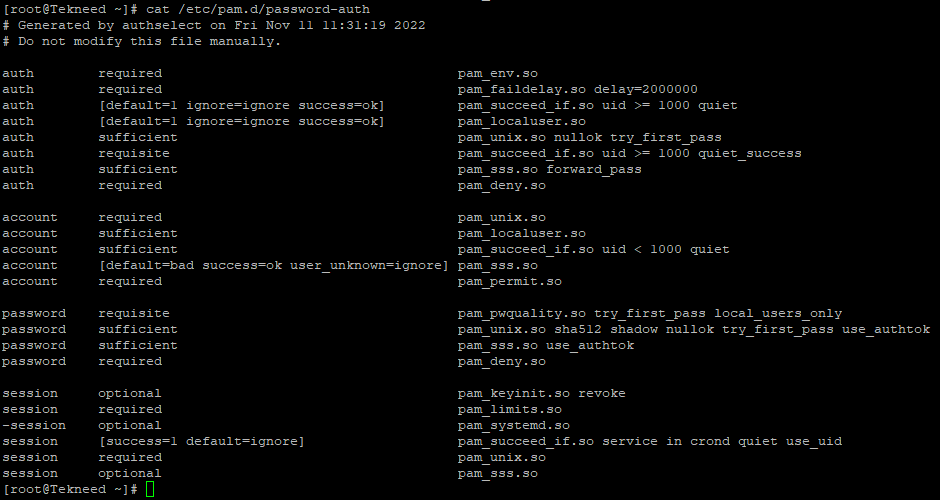
The /etc/pam.d/system-auth and the /etc/pam.d/password-auth file will usually look like the pictures below. However, you might see a slight changes depending on the Linux distribution.
[root@Tekneed ~]# cat /etc/pam.d/system-auth
[root@Tekneed ~]# cat /etc/pam.d/password-auth
*** Its a good practice to backup these two important files ***
[root@Tekneed ~]# cp /etc/pam.d/system-auth /etc/pam.d/system-auth_backup[root@Tekneed ~]# cp /etc/pam.d/password-auth /etc/pam.d/password-auth_backupMethod 1
Editing the pam.d configuration files manually (/etc/pam.d/system-auth and /etc/pam.d/password-auth)
1. Edit the /etc/pam.d/system-auth file by adding the following parameters below
Please note that the parameters in this files are executed in their order, so be careful to add the parameters in the correct lines as shown in the picture below.
Its also a good practice to always backup an orginal file before editing.
[root@Tekneed ~]# vi /etc/pam.d/system-auth
auth required pam_faillock.so preauth silent deny=3 unlock_timeout=600
auth required pam_faillock.so authfail deny=3 unlock_timeout=600
account required pam_faillock.so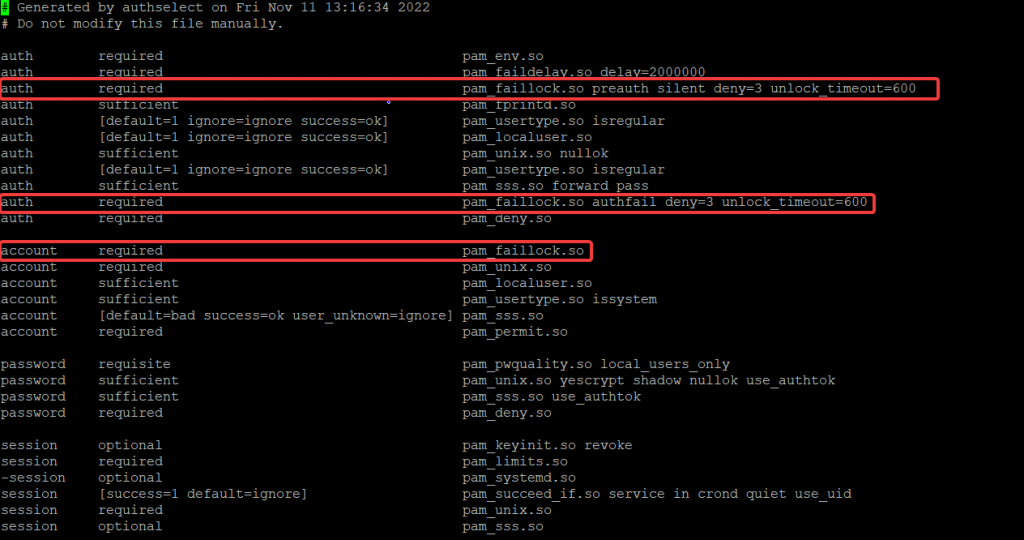
The option/argument, (deny=3 unlock_timeout=600) means that after 3 times of failed password trial, the user account should be locked for 600 seconds (10 minutes)
Note that this is not applicable to the root user. If you also want this settings to be applicable to the root user, you also need to add the parameter, “even_deny_root“
2. Edit the /etc/pam.d/password-auth file by adding the following parameters below:
it’s a good practice to always backup an original file before editing.
[root@Tekneed ~]# vi /etc/pam.d/password-auth
auth required pam_faillock.so preauth silent deny=3 unlock_timeout=600
auth required pam_faillock.so authfail deny=3 unlock_timeout=600
account required pam_faillock.so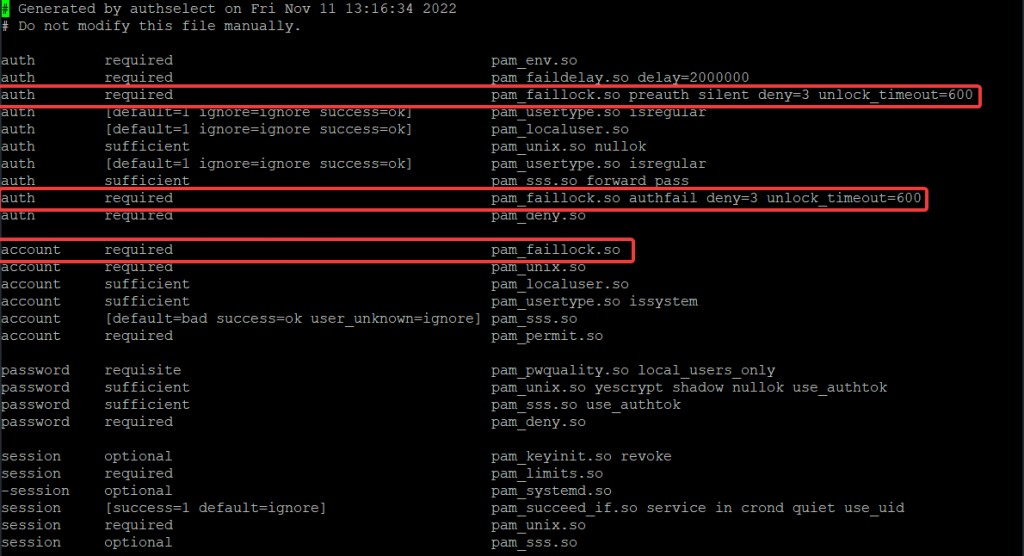
3. You can test with your users.
**To disable pam_faillock manually, delete the parameters added in the /etc/pam.d configuration file**
Method 2 (Recommended)
Editing the pam.d configuration file by using the authselect tool (/etc/pam.d/system-auth and /etc/pam.d/password-auth)
The authselect tool and PAM must be updated to the version below or higher.
authselect-1.2.1-2.el8
pam-1.3.1-8.el81. Verify the authselect and pam version.
[root@Tekneed ~]# rpm -q authselect
authselect-1.1-2.el8.x86_64
[root@Tekneed ~]# rpm -q pam
pam-1.3.1-4.el8.x86_64
2. Upgrade authselect and pam
[root@Tekneed ~]# dnf upgrade authselect pam -y
Updating Subscription Management repositories.
Red Hat Enterprise Linux 8 for x86_64 - BaseOS (RPMs) 514 kB/s | 55 MB 01:49
................................
Installed products updated.
Upgraded:
pam-1.3.1-22.el8.x86_64 authselect-1.2.5-1.el8.x86_64 authselect-libs-1.2.5-1.el8.x86_64 authselect-compat-1.2.5-1.el8.x86_64
Complete!
3. Verifythat both packages have been upgraded
[root@Tekneed ~]# rpm -q authselect pam
authselect-1.2.5-1.el8.x86_64
pam-1.3.1-22.el8.x86_644. Enable the faillock feature.
[root@Tekneed ~]# authselect enable-feature with-faillock
Make sure that SSSD service is configured and enabled. See SSSD documentation for more information.If you check the /etc/pam.d/system-auth file, and the /etc/pam.d/password-auth files, you will notice that the files have been automatically updated
[root@Tekneed ~]# grep -i faillock /etc/pam.d/{system-auth,password-auth}
/etc/pam.d/system-auth:auth required pam_faillock.so preauth silent
/etc/pam.d/system-auth:auth required pam_faillock.so authfail
/etc/pam.d/system-auth:account required pam_faillock.so
/etc/pam.d/password-auth:auth required pam_faillock.so preauth silent
/etc/pam.d/password-auth:auth required pam_faillock.so authfail
/etc/pam.d/password-auth:account required pam_faillock.so
5. Configure faillock
The options to configure faillock is stored in /etc/security/faillock.conf. The options we are going to use un our case are;
silent
deny=3
unlock_time=600Uncomment the following parameters or edit accordingly as you want in the /etc/security/faillock.conf file.
[root@Tekneed ~]# vi /etc/security/faillock.conf
silent
deny=3
unlock_time=600If you also want this settings to be applied to the root user too, you can also uncomment the “even_deny_root” option in the /etc/security/faillock.conf file.
6. If you wish, you can test with your users by trying to login when attempted login has failed 3 times.
[bola@Tekneed ~]$ su - tayo
Password:
su: Authentication failure
[bola@Tekneed ~]$ su - tayo
Password:
su: Authentication failure
[bola@Tekneed ~]$ su - tayo
Password:
su: Authentication failure
[bola@Tekneed ~]$ su - tayo
Password:
***To list the failed login counters, use the command below
[root@Tekneed ~]# faillock
bola:
When Type Source Valid
tayo:
When Type Source Valid
2022-11-13 22:20:20 TTY pts/3 V
2022-11-13 22:20:26 TTY pts/3 V
2022-11-13 22:20:33 TTY pts/3 V
***To list failed login counters for a specific user, use the command below.
[root@Tekneed ~]# faillock --user lisa
lisa:
When Type Source Valid
2022-11-13 22:08:31 TTY pts/3 V
2022-11-13 22:08:40 TTY pts/3 V
2022-11-13 22:08:48 TTY pts/3 V
You can also check the /var/log/secure file by using the command below.
[root@Tekneed ~]# tail -f /var/log/secure
Nov 13 22:08:48 Tekneed su[29085]: pam_faillock(su-l:auth): Consecutive login failures for user tayo account temporaril y locked
Nov 13 22:20:20 Tekneed unix_chkpwd[29136]: password check failed for user (tayo)
Nov 13 22:20:20 Tekneed su[29132]: pam_unix(su-l:auth): authentication failure; logname=bola uid=1002 euid=0 tty=pts/3 ruser=bola rhost= user=tayo
Nov 13 22:20:33 Tekneed su[29140]: pam_faillock(su-l:auth): Consecutive login failures for user tayo account temporaril y locked
Nov 13 22:20:41 Tekneed unix_chkpwd[29145]: password check failed for user (tayo)
Nov 13 22:20:41 Tekneed su[29143]: pam_unix(su-l:auth): authentication failure; logname=bola uid=1002 euid=0 tty=pts/3 ruser=bola rhost= user=tayo
............................
***To unlock a user, use the command below.
[root@Tekneed ~]# faillock --reset --user lisa
***To unlock all users, use the command below.
[root@Tekneed ~]# faillock --resetTo disable faillock with authselect, use the command below.
[root@Tekneed ~]# authselect disable-feature with-faillock
***To learn more about pam_faillock, you can check the man page
[root@Tekneed ~]# man pam_faillock
[root@Tekneed ~]# man faillockMethod 3
Editing the pam.d configuration file by using the authconfig tool (/etc/pam.d/system-auth and /etc/pam.d/password-auth)
The authconfig tool is deprecated and replaced with authselect but still works though.
1. Use the authconfig tool to configure faillock.
[root@Tekneed ~]# authconfig --enablefaillock --faillockargs="deny=3 unlock_timeout=600" --update
Running authconfig compatibility tool.
The purpose of this tool is to enable authentication against chosen services with authselect and minimum configuration. It does not provide all capabilities of authconfig.
IMPORTANT: authconfig is replaced by authselect, please update your scripts.
See man authselect-migration(7) to help you with migration to authselect
Warning: These options are not supported anymore and have no effect:
--faillockargs
Executing: /usr/bin/authselect check
Executing: /usr/bin/authselect current --raw
Executing: /usr/bin/authselect select sssd with-silent-lastlog with-fingerprint with-faillock --force
2. Verify that the /etc/pam.d/system-auth file and the /etc/pam.d/password-auth file has been updated.
[root@Tekneed ~]# grep -i faillock /etc/pam.d/system-auth
auth required pam_faillock.so preauth silent
auth required pam_faillock.so authfail
account required pam_faillock.so
[root@Tekneed ~]# grep -i faillock /etc/pam.d/password-auth
auth required pam_faillock.so preauth silent
auth required pam_faillock.so authfail
account required pam_faillock.so
OR
[root@Tekneed ~]# grep -i faillock /etc/pam.d/{system-auth,password-auth}
/etc/pam.d/system-auth:auth required pam_faillock.so preauth silent
/etc/pam.d/system-auth:auth required pam_faillock.so authfail
/etc/pam.d/system-auth:account required pam_faillock.so
/etc/pam.d/password-auth:auth required pam_faillock.so preauth silent
/etc/pam.d/password-auth:auth required pam_faillock.so authfail
/etc/pam.d/password-auth:account required pam_faillock.so
3. Verify that faillock has been configured by authconfig
[root@Tekneed ~]# grep -i faillock /etc/sysconfig/authconfig
USEFAILLOCK=yes
FAILLOCKARGS="deny=3 unlock_timeout=600"
To disable faillock with authconfig, use the command below.
[root@Tekneed ~]# authconfig --disablefaillock --update
Running authconfig compatibility tool.
The purpose of this tool is to enable authentication against chosen services with authselect and minimum configuration. It does not provide all capabilities of authconfig.
IMPORTANT: authconfig is replaced by authselect, please update your scripts.
See man authselect-migration(7) to help you with migration to authselect
Executing: /usr/bin/authselect check
Executing: /usr/bin/authselect current --raw
Executing: /usr/bin/authselect select sssd with-silent-lastlog with-fingerprint --force
To verify that faillock has been disabled by authconfig, you can run these commands again.
[root@Tekneed ~]# grep -ii faillock /etc/pam.d/{system-auth,password-auth}
[root@Tekneed ~]#
[root@Tekneed ~]# grep -i faillock /etc/sysconfig/authconfig
USEFAILLOCK=no
FAILLOCKARGS="deny="3 unlock_timeout=600""
Click Here To Watch Video On How To Lock User Account In Linux After Failed Login Attempts
Your feedback is welcomed. If you love others, you will share with others
Small Correction in method 1:
Instead of unlock_timeout=600 use unlock_time=600 everywhere.
unlock_timeout is unsupported format in RHEL 8.
Thanks.
Editing the pam.d configuration files manually (/etc/pam.d/system-auth and /etc/pam.d/password-auth)