This tutorial is focused on what SSH is, how to change SSH port from default 22 to the desired port and why you may want to consider to change the port. It also guides you on how to disable the root login for SSH
UNDERSTANDING THE SUBJECT MATTER
SSH means secure shell, From the word secured, it is a network protocol that allows a remote connection to a server securely.
Not to go out of the scope of this study, I will briefly talk on the history of SSH.
Prior to using the SSH protocol, telnet known as Telecommunications and Networks was formerly used to remotely log into servers, it uses a default port 23 and it’s best used for Unix-like operating systems. To login into a Linux server using telnet, the telnet command can simply be launched from the windows command line by typing
telnet <hostname> or telnet <IP address of the server>.
For example, if you had to connect to a Linux system with the IP address 10.10.10.22, you need to type the following command at the command line.
<telnet 10.10.10.22>, a login prompt to type the login username and password will be displayed and if authenticated, you will be connected to the server.
However, as the years go by and technology began to advance, the telnet protocol became unsecured because it doesn’t use any security algorithm to transfer data, no form of encryption, it just transfers data in a plain text and hackers uses this medium to get vital information including usernames and passwords. Hence why the SSH protocol was developed in the year 1995 by Tatu Ylonen, a native of Finland when his university network became a victim of a password sniffing attack to replace telnet and other unsecured protocols like rsh, rlogin and the likes.
The SSH protocol is the most used network protocol for a remote connection. It uses a default port 22 and has an encryption mechanism incorporated into it. So when there is communication between two servers via SSH, the transferred data is protected which prevents sniffing and any other form of other unpleasant activities. SSH has a lot of features and flexibility.
The SSH configuration files is found in “/etc/ssh”
[root@rhel8 ~]# cd /etc/ssh
[root@rhel8 ssh]# ls
moduli ssh_host_ecdsa_key ssh_host_rsa_key
ssh_config ssh_host_ecdsa_key.pub ssh_host_rsa_key.pub
ssh_config.d ssh_host_ed25519_key
sshd_config ssh_host_ed25519_key.pub
[root@rhel8 ssh]#
The SSH default port and disabling of the root login for SSH can be changed in the /etc/ssh/sshd_config file
The first time the client (SSH client) tries to connect to the remote server (SSH server), the ssh service (sshd daemon) on the server is notified on the incoming request.
More so, the client probes the server to prove it’s identity, for the identity to be proven, the key fingerprint which is the public key found in the /etc/ssh/ssh_host.pub file on the server is immediately sent to the client in this format,
The authenticity of host ‘localhost (::1)’ can’t be established.
ECDSA key fingerprint is SHA256:gKULY7EQidV5q2zxj/ZqWAyQHfF9j2gmnX9DnVySv6o.
ECDSA key fingerprint is MD5:e7:e4:c2:0a:c8:19:9f:a3:c3:66:e3:25:b6:43:60:6d.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added ‘localhost’ (ECDSA) to the list of known hosts.
root@localhost’s password:
Because it is the first time both systems will be connecting, the client will not recognize the public keys. However, a warning message is given as displayed in the format above.
"Are you sure you want to continue (yes/no)? yes
if the client is sure she wants to connect, the client type “yes” to continue and the public key is immediately stored on the client’s home directory in the file (~/.ssh/known_hosts).
More so, the server also needs to verify it’s identity from the client by telling the client to input the password, if the account (credentials) is verified and correct, authentication to the server will be possible but if the credential is wrong, authentication to the server will be denied.
This is one of the security mechanisms used by SSH.
The second time the clients want to connect to the server, since the public key is already stored by the client for the first time, the client does not require the server to prove it’s identity anymore and the client will only be prompted to input the server’s credentials for authentication.
now let’s practical by trying to login to a remote server via the SSH protocol
To remotely connect to a Linux server, you use the command ssh. For example, if you want to connect remotely to server B (rhel7) from server A (rhel8), you will need to do the following.
- Get the IP address or the host name of the server you want to connect to, in this case, the server’s host name is rhel7 and the IP address is 192.168.170.141
[root@rhel7 ~]# ip a
1: lo:
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33:
link/ether 00:0c:29:dc:f5:94 brd ff:ff:ff:ff:ff:ff
inet 192.168.170.141/24 brd 192.168.170.255 scope global noprefixroute dynamic ens33
valid_lft 1434sec preferred_lft 1434sec
inet6 fe80::5353:948b:670:3326/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@rhel7 ~]#
- After getting the IP, connect to the server from the client (rhel8) by using the following command.
ssh <username@server's-IP>
[root@rhel8 ~]# ssh root@192.168.170.141
The authenticity of host ‘192.168.170.141 (192.168.170.141)’ can’t be establishe d.
ECDSA key fingerprint is SHA256:gKULY7EQidV5q2zxj/ZqWAyQHfF9j2gmnX9DnVySv6o.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added ‘192.168.170.141’ (ECDSA) to the list of known hosts.
root@192.168.170.141’s password:
Last login: Thu Jan 2 17:13:11 2020 from 192.168.170.1
[root@rhel7 ~]#
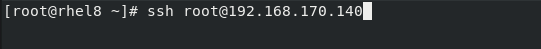
And boom!!! you are in.
What if your server is configured to use a port number different from the default port 22. For example, if you want to connect remotely to server B (rhel8) that is using SSH port 2019 from server A (rhel7), you will need to do the following.
- Get the IP address or the host name of the server you want to connect to, in this case, the server’s host name is rhel8 and the IP address is 192.168.170.129
[root@rhel8 ~]# ip a
1: lo:
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33:
link/ether 00:0c:29:35:48:0c brd ff:ff:ff:ff:ff:ff
inet 192.168.170.129/24 brd 192.168.170.255 scope global dynamic noprefixroute ens33
valid_lft 1423sec preferred_lft 1423sec
inet6 fe80::338b:befc:f3a2:f6e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: virbr0:
link/ether 52:54:00:8d:6d:4e brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic:
link/ether 52:54:00:8d:6d:4e brd ff:ff:ff:ff:ff:ff
- After getting the IP, connect to the server from the client (rhel7) by using the following command.
ssh -p <port-no> <username@server's-IP>
[root@rhel7 ~]# ssh -p 2019 root@192.168.170.129
The authenticity of host ‘[192.168.170.129]:2019 ([192.168.170.129]:2019)’ can’t be established.
ECDSA key fingerprint is SHA256:H+yWeopzYgotpIAES+pEO6sFjE1/6iGvkOvmLfSN7wY.
ECDSA key fingerprint is MD5:38:bb:03:4d:4d:94:52:30:42:ac:77:66:3e:72:ac:5b.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added ‘[192.168.170.129]:2019’ (ECDSA) to the list of known hosts.
root@192.168.170.129’s password:
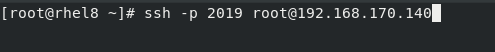
you can use the command ssh –help to get more options
To connect to a Linux server via SSH from a Windows machine, you will need an SSH client application like Putty, Bitvise, etc. Personally, I use putty or bitvise.
You can download putty via this link . https://www.putty.org/ (About 3.5mb)
After downloading, you will need to

The major reason the SSH default port is most times changed by administrators is to tighten the security of the server more especially when the server is internet facing. Virtually every Tech person knows the SSH default port including the bad guys (hackers), though SSH is secured but to double secure your environment, the SSH default port 22 can be changed to any desired port. In the “ACTION TIME” section, the SSH default port was changed to port 2019.
More so, the root login can be disabled for SSH. These actions are for security purposes. In the advent of a brute force attack, the attacker will not have the full rights and privileges for any unpleasant activities. Hence, damages may be limited.
ACTION TIME
STEPS
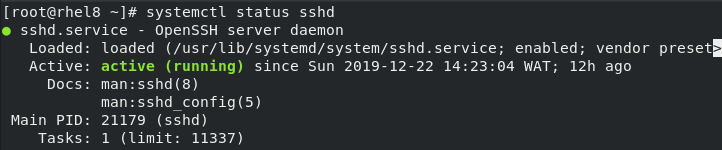
- Confirm the sshd service status
# systemctl status sshd
2. Edit the /etc/ssh/sshd_config file. Search for Port 22 and add the new port immediately after.
# vi /etc/ssh/ssshd_config
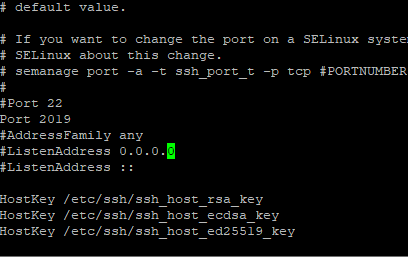
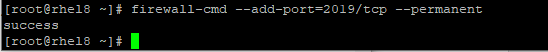
3. Add the new port to the firewall rule
# firewall-cmd –add-port=2019/tcp –permanent
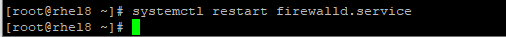
4. restart the firewall service.
# systemctl restart firewalld.service
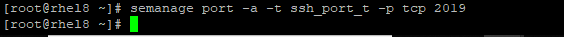
5. Manage the SELinux policy by adding the new port to the SSH program for SELinux .
# semanage port –a –t ssh_port_t –p tcp 2019
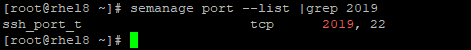
6. verify the type context to see if port 2019 is allowed
# semanage port –list |grep 2019
7. Restart the ssh service
# systemctl restart sshd.service
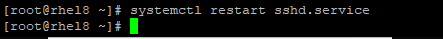
8. Login with the new port.
STEPS
- Edit the /etc/ssh/sshd_config file. Search for the line PermitRootLogin and change yes to no.
# vi /etc/ssh/ssshd_config
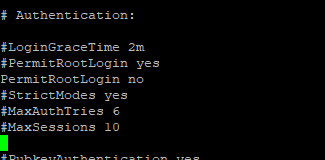
2. Restart the ssh service.
# systemctl restart sshd.service
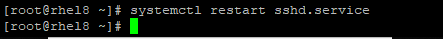
3. Login as root and access will be denied.
Thanks.
I just followed the steps and I was able to change mine. Step is direct and straight forward.
nicely written. Thanks
Thanks
Nice article.
wow! Finland gave us SSH as well as Linux. Thanks for the narrative in these lessons.