understand how a firewall works in Linux, how to configure and manage firewall in Linux. You will also learn firewall settings & how to identify firewall rules, etc.
UNDERSTANDING THE SUBJECT MATTER
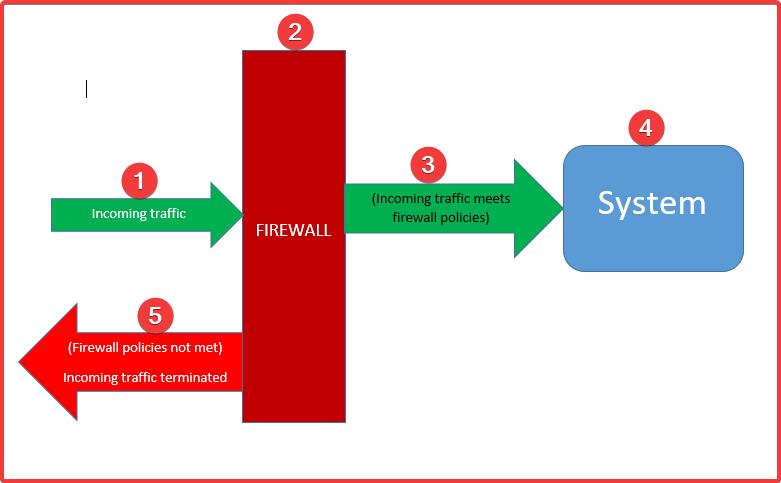
A firewall is a security feature that is used to protect a system from incoming network traffic.
A system can be protected from incoming traffic by defining or adding rules or set of rules to a firewall. These rules are called firewall rules.
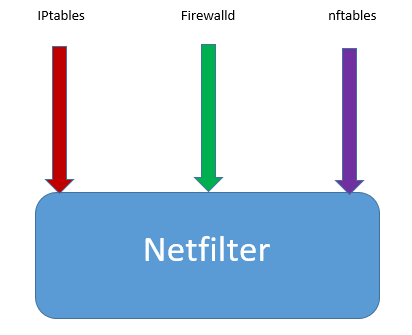
In Linux, you may have heard about iptables, firewalld, and nftables. All these are firewall tools that are used to manage netfilters.
As they say, there is no smoke without fire. The same way you cannot mention firewall in Linux without mentioning netfilter.
A netfilter is a framework in the Linux kernel used to address network functionalities such as packet filtering, network address translation, port translation, etc.
In other words, the function of a netfilter is to address a firewall, and the netfilter can be managed via iptables, firewalld or nftables firewall tools.
The iptables tool is a very common tool in managing firewall in Linux. It has been in existence for a long time and will still very much likely be.
However, some Linux distributions like Red Hat 7 and CentOS 7 by default now use firewalld. As a matter of fact, iptables have been totally deprecated in some Linux distributions like Red Hat 8, and CentOS 8.
The firewall tools used in managing netfilter in these distributions are now firewalld and nftables.
Firewalld can be used to configure non-advanced firewall rules, while nftables is used to configure a very advanced firewall rule.
In this tutorial, we will look at how to use firewalld to manage firewall, also, in the second part of this tutorial, we will look at how to configure nftables to manage firewall.
firewalld works with a zone and service technique.
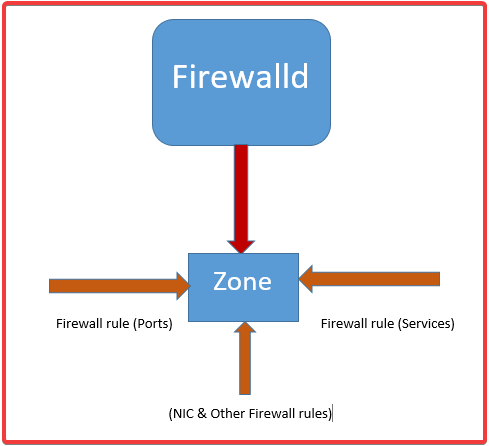
A zone is created and activated, on the zone is where the firewall rules will be defined, and firewall rules include allowing sets of IP’s, protocols/ports, NICs, etc.
Firewall rules can be defined/configured directly on the zone or can be defined by creating a service, and then attaching the service to the zone.
We are going to see how all of these can be done with examples as we go on.
Let’s understand what zone(s) and service(s) is
Firewalld Zone
A zone is a firewall feature where a set of firewall rules is configured on. The zone concept in firewalld has made firewall management, as well as traffic management easy compared to iptables.
With zone, a lot of complex firewall rules can be easily configured on the system by activating as many zones as possible to suit a firewall need.
Zones can be created by a user but there are already predefined zones on the system that are suitable for their purposes or a lot of puropses. So, an admin can either create their own zone(s) or choose to use one of the predefined zones on the system.
The predefined zone(s) can be configured to suit a firewall need.
The predefined zones can be seen on the system by using the command,
[root@HQDEV1 ~]# firewall-cmd --get-zones
block dmz drop external home internal libvirt public trusted workOn my system, RHEL 8, there are ten predefined zones by default as seen in the output of the command above. So whatever network traffic that must be allowed on the system must be configured on the active zone(s).
The predefined zones location is in /usr/lib/firewalld/zones.
If you change directory to this location and do ls, you will see all the configuration files associated with these zones.
[root@DRDEV1 ~]# cd /usr/lib/firewalld/zones/
[root@DRDEV1 zones]# ls
block.xml drop.xml home.xml libvirt.xml trusted.xml
dmz.xml external.xml internal.xml public.xml work.xmlWhat are these predefined zones suitable for?
- block zone is suitable for incoming connections/traffic that is not trusted, this zone blocks all incoming traffic with “ICMP prohibited message”. Only the network traffic that meets the specified firewall rules condition on this zone can be allowed into the system
- drop zone is also suitable for incoming connections/traffic that is not trusted at all, this zone also blocks all incoming traffic but with no message. This zone makes intruding hard because no error or a particular message can be traced. Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system
- dmz zone (demilitarize zone) is suitable for public network or internet–facing systems with limited access. Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system
- Public zone is suitable for public network or internet-facing systems. Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system. This zone is an active and the default zone in Linux.
- External zone is suitable for external network and masquerading, it is very suitable for a network that is used for routers. Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system
- Home zone is suitable for a home network, that is, network within your home environment. network within this sphere can be trusted. However, Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system
- internal zone is suitable for an internal network, incoming network within this environment can also be trusted. However, Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system
- Trusted Zone is suitable for a trusted network, this zone allows all incoming connections without filtering anything. This zone should only be used if you trust every incoming connection without any doubt
- work zone is suitable for work network, that is, network within your working environment. Still, Only the network traffic that meets the firewall rules condition on this zone can be allowed into the system
- libvirt zone is suitable for virtualization network, libvirtd is the daemon responsible for KVM virtualization.
Just as I mentioned, the default zone is the public zone, and, of course, an active zone.
To verify all the active zones on a Linux system
Use the command,
[root@HQDEV1 ~]# firewall-cmd --get-active-zones
libvirt
interfaces: virbr0
public
interfaces: ens33To verify the default zone,
use the command,
[root@HQDEV1 ~]# firewall-cmd --get-default-zone
public
From the output above, the default zone is the public zone. So, whatever firewall rules you are configuring is applied to this zone because it is the default except it is specified which zone you want the configurations to apply to.
The default zone can be changed if an administrator wishes to.
To verify the default zone & its rules/configurations,
use the command,
[root@HQDEV1 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens33
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
You can also see every configurations/firewall rules such as services, ports, interfaces, etc configured/defined on this zone.
To list all zones available on the system with their rules/configuration,
use the command,
[root@HQDEV1 ~]# firewall-cmd --list-all-zones
block
target: %%REJECT%%
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
dmz
target: default
icmp-block-inversion: no
interfaces:
sources:
services: ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
drop
target: DROP
icmp-block-inversion: no
interfaces:
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
......................................
To list a specific zone with its rules/configuration,
use the command,
# firewall-cmd --zone=<zone-name> --list-all[root@HQDEV1 ~]# firewall-cmd --zone=public --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens33
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
To change the default zone
use the command,
# firewall-cmd --set-default-zone <zone-name>For example, to change the default zone to home, use the command,
[root@HQDEV1 ~]# firewall-cmd --set-default-zone home
successHaving understood zones, let us understand what a firewalld service is before we look at some firewall configuration examples.
Firewalld Services
firewalld services in this context is a technique firewalld uses to define a firewall rule. It is a very simple concept.
The combination of ports, protocols, and sometimes IPV4 and IPV6 destination entries makes a service. This service can then be attached to a zone.
Just as there are predefined zones, there are also predefined services. So, an administrator can choose to create their service(s) or make do of the predefined ones.
The predefined services can be seen on a Linux system by using the command,
[root@HQDEV1 ~]# firewall-cmd --get-services
RH-Satellite-6 amanda-client amanda-k5-client amqp amqps apcupsd audit bacula bacula-client bb bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc bittorrent-lsd ceph ceph-mon cfengine cockpit condor-collector ctdb dhcp dhcpv6 dhcpv6-client distcc dns dns-over-tls docker-registry docker-swarm dropbox-lansync elasticsearch etcd-client etcd-server finger freeipa-4 freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp
...............On my system in this case, RHEL 8, there are a lot of predefined services by default as seen in the output of the command above.
The predefined services location is in (/usr/lib/firewalld/services)
To see all the services and their information, you can navigate to this location.
[root@HQDEV1 services]# cd /usr/lib/firewalld/services[root@HQDEV1 services]# ls -l
-rw-r--r--. 1 root root 412 Aug 13 2019 amanda-client.xml
-rw-r--r--. 1 root root 447 Aug 13 2019 amanda-k5-client.xml
-rw-r--r--. 1 root root 283 Aug 13 2019 amqps.xml
-rw-r--r--. 1 root root 273 Aug 13 2019 amqp.xml
-rw-r--r--. 1 root root 285 Aug 13 2019 apcupsd.xml
-rw-r--r--. 1 root root 301 Aug 13 2019 audit.xml
-rw-r--r--. 1 root root 320 Aug 13 2019 bacula-client.xml
-rw-r--r--. 1 root root 227 Aug 13 2019 dhcp.xml
-rw-r--r--. 1 root root 353 Aug 13 2019 http.xml
-rw-r--r--. 1 root root 461 Aug 13 2019 samba.xml
.......To see the samba.xml file for example, use the command,
[root@HQDEV1 services]# cat samba.xml
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>Samba</short>
<description>This option allows you to access and participate in Windows file and printer sharing networks. You need the samba package installed for this option to be useful.</description>
<port protocol="udp" port="137"/>
<port protocol="udp" port="138"/>
<port protocol="tcp" port="139"/>
<port protocol="tcp" port="445"/>
<module name="nf_conntrack_netbios_ns"/>
</service>
you can now see how a firewalld service file looks like. Like I also mentioned, you can create a service if you don’t want to use the predefined one and attach it to a zone.
How To Create a Firewalld Service
To create a service, you will need to follow the XML template just as the ones in the predefined service’s templates.
However, the best practice is that an administrator will create their services in the location, (/etc/firewalld/services) and not (/usr/lib/firewalld/services)
For example, to create a tekneed service where port 2020 and the protocol TCP and UDP will be allowed, use one of the predefined services XML templates by following the steps below.
1. copy one of the predefined XML service templates to create your own
NOTE: extension must be (.xml)
[root@HQDEV1 ~]# cp /usr/lib/firewalld/services/samba.xml /etc/firewalld/services/tekneed.xml
2. edit the template to suit what you want
[root@HQDEV1 ~]# vi /etc/firewalld/services/tekneed.xml<?xml version="1.0" encoding="utf-8"?>
<service>
<short>Tekneed</short>
<description>This option is for a tekneed service based on this article.</description>
<port protocol="udp" port="2020"/>
<port protocol="tcp" port="2020"/>
</service>when you create a firewalld service, the next thing, of course, is to attach the service to a zone, but before we look at how a service can be attached to a zone and how firewall can be configured, let’s understand the process again.
1. Network traffic from a source is sent into the system, if firewalld is enabled, firewalld checks the firewall rules defined/attached on the active zone(s) to see if the incoming traffic meets the conditions defined on the zones.
NOTE: More than one zone can be configured to be active on the system irrespective of the number of NICs
2. If the firewall rules conditions are met, network traffic is allowed into the system, but if not, network traffic is denied
NOTE: These firewall rules are defined/configured on the zone, and can either be defined directly on the zone or can be defined by creating a service or services, and then attaching the service(s) to the zones.
Keynotes
- You can create a zone or use a predefined zone
- The default zone is the public zone, and it can be changed.
- The active zones have an active NICs attached to them and the libvirt zone is an active zone by default. The libvirt zone is a special type of zone that is used specifically for virtualization, and by default, the virtual NIC is attached to this zone.
- you can attach a predefined service(s) to a zone and/or create a services(s), then attach it to a zone.
- Defining firewall rules on a zone actually means configuring a firewall on the system. Therefore, let’s look at how to configure firewall on a Linux system using firewalld
ACTION TIME
How To Configure Firewall In Linux Using Firewalld
I have mentioned in the “UNDERSTANDING THE SUBJECT MATTER” section that firewalld is the default firewall program that comes with RHEL 7 & 8 systems.
However, if your distribution is not shipped with firewalld, it can be installed because the firewalld must be up and running to be able to configure firewall in Linux using firewalld.
How To Install Firewalld
To install firewalld, use the command,
[root@HQDEV1 ~]# yum install firewalldHow To Verify / Check Firewall Status In Linux
To verify if firewall is running, use the command,
[root@HQDEV1 ~]# systemctl status firewalld.service
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2020-05-15 10:04:18 WAT; 4min 21s ago 
How To Start / Open Firewall In Linux
To start firewall in Linux, use the command
[root@HQDEV1 ~]# systemctl start firewalld
How To Enable Firewall On Linux
To enable firewall in Linux, use the command below. using this command means that the firewalld daemon/service will be persistent after reboot
[root@HQDEV1 ~]# systemctl enable firewalldHow To Stop Firewall In Linux
To stop firewall in Linux, use the command,
[root@HQDEV1 ~]# systemctl stop firewalldHow To Disable Firewall In Linux
To disable firewall in Linux, use the command below. Using this command means that the firewalld daemon/service will not be persistent after a reboot.
[root@HQDEV1 ~]# systemctl disable firewalld.serviceI have mentioned in the “UNDERSTANDING THE SUBJECT MATTER” section that firewall configuration means defining firewall rules on zone(s)
How To Add a Port /Open a Port On Firewall In Linux
To open a port on a firewall, use the command,
# firewall-cmd --add-port=<port-no/protocol>- For example, to add port 2022/tcp to the firewall rule, use the command
[root@HQDEV1 ~]# firewall-cmd --add-port=2022/tcp
success
- To make the changes permanent, use the command,
[root@HQDEV1 ~]# firewall-cmd --add-port=2022/tcp --permanent- You may want to reload firewalld
[root@HQDEV1 ~]# firewall-cmd --reload
success- Verify if the port has been added
[root@HQDEV1 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens33
sources:
services: cockpit dhcpv6-client ssh
ports: 2022/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
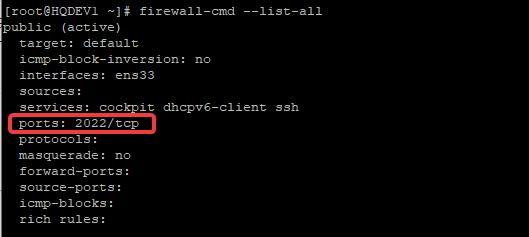
As I have mentioned in the “UNDERSTANDING THE SUBJECT MATTER” section, if you don’t specify the zone you want to apply a configuration to, it is automatically applied to the default zone. It has been confirmed now. Let’s specify a zone.
How To Add a Port /Open a Port On Firewall In Linux On a Specific Zone
To open a port on a specific zone, use the command,
firewall-cmd --zone=<zone-name> --add-port=<port-no/protocol>- For example, to open port 2023/udp on home zone, use the command,
[root@HQDEV1 ~]# firewall-cmd --zone=home --add-port=2023/udp --permanentYou may want to reload firewalld
[root@HQDEV1 ~]# firewall-cmd --reload- Verify if the port has been opened on the zone
[root@HQDEV1 ~]# firewall-cmd --zone=home --list-allHow To Remove / Close a Port On Firewall In Linux
To close a port, replace the add parameter with remove.
firewall-cmd --remove-port=<port-no/protocol> --permanent- For example, to remove/close port 2023/tcp on the public zone, use the command,
[root@HQDEV1 ~]# firewall-cmd --zone=public --remove-port=2023/tcp --permanent
success
How To Verify Which NIC (Network Interface Card) Is Associated With a Zone
To verify which NIC is attached to a zone, use the command,
# firewall-cmd --get-zone-of-interface=<NIC>[root@HQDEV1 ~]# firewall-cmd --get-zone-of-interface=ens33
public
How To Reassign a NIC To A Different Zone
To reassign a NIC to a different zone, use the command,
# firewall-cmd --change-interface=<NIC> --zone<zone-name> --permanentExample
[root@HQDEV1 ~]# firewall-cmd --change-interface=ens33 --zone=home --permanent
The interface is under control of NetworkManager, setting zone to 'home'.
success[root@HQDEV1 ~]# firewall-cmd --reload[root@HQDEV1 ~]# firewall-cmd --get-zone-of-interface=ens33
homeI have mentioned in the “UNDERSTANDING THE SUBJECT MATTER” section that service is the combination of a port(s) and protocol(s) entries, and adding a service to a firewall means adding firewall rules to a zone.
To add a service to a firewall, use the command,
# firewall-cmd --add-service=<service-name>- For example, to add the samba service to firewall, use the command,
[root@HQDEV1 ~]# firewall-cmd --add-service=samba- To make it permanent, use the command,
[root@HQDEV1 ~]# firewall-cmd --add-service=samba --permanent
success
- You may want to reload firewalld
[root@HQDEV1 ~]# firewall-cmd --reload
success- To attach a service to a specific zone, use the command,
[root@HQDEV1 ~]# firewall-cmd --zone=home --add-service=samba --permanent
successHow To Remove A Service From A Firewall / Zone
To remove a service froma firewall / zone, replace the “–add service” command with “–remove service” command
firewall-cmd --remove-service=<service-name> --permanentAdvanced Firewall Configuration and Management part 2 (To be continued…)
Class Activity
1. is iptables a firewall?
RHCSA 8 Exam Practice Question & Answer On Managing Firewall In Linux
Your feedback is welcomed. If you love others, you will share with others
J’avoue que cette page web ma beaucoup aidé
Merci beaucoup
vous êtes les bienvenus