Last updated: June 2020
Learn how to encrypt a drive in Linux, the step by step process of how to encrypt a partition and check if a disk or filesystem is encrypted using “cryptsetup”.
Contents
A way to secure a file or files is to encrypt a drive or partitions (both standard and LVM partitions).
Drives or partitions in Linux can be encrypted in various formats and with various tools.
In this lesson, we will look at the step by step process of how drives/partitions can be encrypted with the “cryptsetup” tool using LUKS (Linux unified key setup).
How To Encrypt a Drive / Filesystem In Linux With cryptsetup Using LUKS (RHEL 7 & 8)
1. Verify your kernel supports filesystem encryption
[root@HQDEV1 ~]# grep -i config_dm_crypt /boot/config-$(uname -r)
CONFIG_DM_CRYPT=m
The output, (CONFIG_DM_CRYPT=m) confirms the kernel supports filesystem encryption
2. Verify if the “dm_crypt” module is loaded
[root@HQDEV1 ~]# lsmod | grep dm_crypt
dm_crypt 45056 1
dm_mod 151552 11 dm_crypt,dm_log,dm_mirrorIf it is not loaded, load the module[link] by using the command,
[root@HQDEV1 ~]# modprobe dm_crypt3. Install the cryptsetup utility
N:B: You may not need to do this for RHEL 7 and RHEL 8. The tool is shipped with It.
[root@HQDEV1 ~]# yum install cryptsetup4. Verify the device you want to encrypt
[root@HQDEV1 ~]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 15G 0 disk
├─sda1 8:1 0 1G 0 part /boot
└─sda2 8:2 0 14G 0 part
├─rhel-root 253:0 0 12.5G 0 lvm /
└─rhel-swap 253:1 0 1.5G 0 lvm [SWAP]
sdb 8:16 0 5G 0 disk
└─sdb1 8:17 0 250M 0 part
sr0 11:0 1 7.3G 0 rom /run/media/root/RHEL-8-1-0-BaseOS-x86_64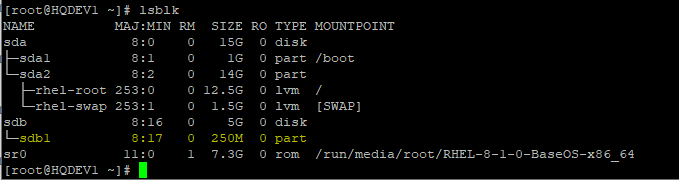
In this case, the device we want to encrypt is (sdb1)
5. Encrypt the device in luks format (Linux unified key)
[root@HQDEV1 ~]# cryptsetup luksFormat /dev/sdb1
WARNING: Device /dev/sdb1 already contains a 'xfs' superblock signature.
WARNING!
========
This will overwrite data on /dev/sdb1 irrevocably.
Are you sure? (Type uppercase yes):
Enter “YES” in uppercase and enter the passphrase
Are you sure? (Type uppercase yes): YES
Enter passphrase for /dev/sdb1:
Verify passphrase:
[root@HQDEV1 ~]#
6. Open the encrypted device with a name
NB: a name of your choice must be included to open the encrypted partition.
cryptsetup luksOpen <device> <name>[root@HQDEV1 ~]# cryptsetup luksOpen /dev/sdb1 tekneed
Enter passphrase for /dev/sdb1:
[root@HQDEV1 ~]#7. Verify in the “/dev/mapper” directory, the encrypted device with the name it was opened with
[root@HQDEV1 ~]# cd /dev/mapper[root@HQDEV1 mapper]# ls
control rhel-root rhel-swap tekneed8. Format the encrypted device with a filesystem type[link]
NB: since the device is encrypted, you can’t just format it directly but the overlay, which is the mapper
[root@HQDEV1 mapper]# mkfs.ext4 /dev/mapper/tekneed
mke2fs 1.44.6 (5-Mar-2019)
Creating filesystem with 239616 1k blocks and 60000 inodes
Filesystem UUID: 8967bff4-3d8e-4c08-86c9-1a1e4cceee9b
Superblock backups stored on blocks:
8193, 24577, 40961, 57345, 73729, 204801, 221185
Allocating group tables: done
Writing inode tables: done
Creating journal (4096 blocks): done
Writing superblocks and filesystem accounting information: done
[root@HQDEV1 mapper]#
9. Create a mount point [link]
[root@HQDEV1]# mkdir /victor10. mount the device
[root@HQDEV1 ~]# mount /dev/mapper/tekneed /victor11. Verify the device is mounted
[root@HQDEV1 ~]# df -Th |grep victor
/dev/mapper/tekneed ext4 223M 2.1M 205M 1% /victor
12. To make the filesystem persistent after reboot, populate the fstab file[link]
[root@HQDEV1 ~]# vi /etc/fstab/dev/mapper/tekneed /victor ext4 defaults 1 213. Populate the crypttab file
[root@HQDEV1 ~]# vi /etc/crypttabtekneed /dev/sdb1 none14. Reboot to test
[root@HQDEV1 ~]# reboot
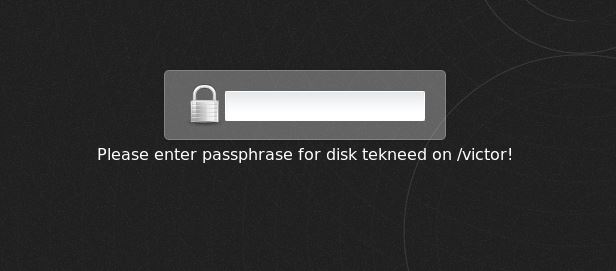
15. Enter the passphrase for the device for boot process to continue
Here is the part where the filesystem is protected, you need to unmount the filesystem and close or disconnect the device when it is not in use.
Let’s see how this can be done
How To Disconnect An Encrypted Device In Linux
Take the following steps to disconnect an encrypted device
1. Unmount the device
[root@HQDEV1 ~]# umount /victor2. disconnect the device
[root@HQDEV1 ~]# cryptsetup luksClose /dev/mapper/tekneed3. Verify the device is disconnected in the “/dev/mapper” directory
[root@HQDEV1 ~]# cd /dev/mapper/;ls
control rhel-root rhel-swap
4. Try to mount the filesystem
[root@HQDEV1 ~]# mount /dev/mapper/tekneed /victor
mount: /victor: special device /dev/mapper/tekneed does not exist.
[root@HQDEV1 ~]#
You can see that the filesystem can’t be mounted. Even if you try to connect the device again, you will be prompted for a passphrase.
More so, you can confirm an encrypted partition by using the command,
#lsblk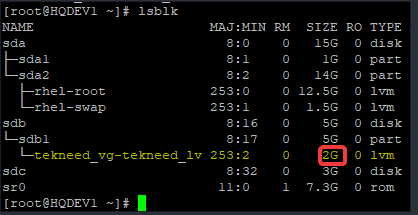
Your feedback is welcomed. If you love others, you will share with others
Leave a Reply