
Welcome To Studying The RHCE/EX294 Series – Ansible Automation!
The Red Hat RHCE course/series is for those who want to further the RHCSA course or learn about the Ansible Automation. For the Linux Fundamentals […]

The Red Hat RHCE course/series is for those who want to further the RHCSA course or learn about the Ansible Automation. For the Linux Fundamentals […]

Linux course for beginners is for those who don’t know anything about Linux and want to start learning, this series has been made to tutor […]

RHCSA 8 & 9 course / series is for those who want to learn Linux, become a Red Hat Enterprise Linux Administrator, or write the […]

There is no excerpt because this is a protected post.

After building a Docker image locally(link), the next big step is pushing it to a registry so it can be pulled, deployed, or shared across […]
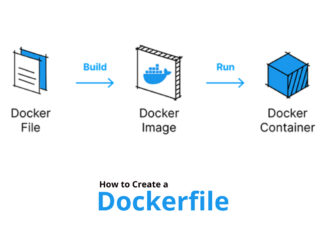

If you are building modern applications, understanding Docker and how to write a dockerfile is essential. At the heart of every Docker image is a […]


Introduction Preparing for the RHCE EX294 exam can be challenging, especially for candidates new to Ansible-based automation exams. Many learners struggle to find reliable, well-structured […]


When applications grow beyond a single container, managing them with long docker run commands becomes difficult. Real-world applications are rarely made up of just one […]
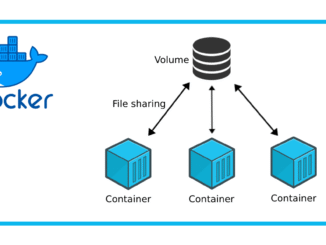

Understanding Docker storage is key to designing reliable, production-ready containerized applications. While containers are lightweight and fast, their storage model is carefully designed to provide […]
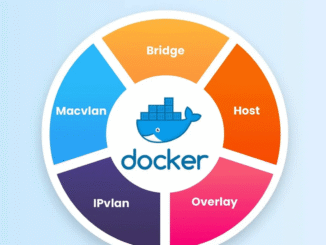

Docker network or Docker Networking is one of those topics that feels mysterious until you actually see what Docker is doing under the hood. In […]



There are so many uses for the vast application of AI in today. Cybersecurity is one sector experiencing a transformation thanks to artificial intelligence (AI) and machine learning (ML). It has changed everything since machine learning (ML) emerged as a tool for identifying, anticipating, and reacting to security threats. We will define these terms and discuss how AI is being applied to improve cybersecurity in this article. What is AI in Cybersecurity? Artificial Intelligence […]


What Is A Cyber Attack? A cyber attack is any attempt by hackers or malicious actors to break into a computer system, network, or digital […]


How do cyber attacks happen? Cyberattacks happen when someone gains unauthorized access to your devices, accounts, or data, often by exploiting human error, lax security, […]
Copyright © 2026 | Tekneed All Rights Reserved