Last updated: March 2022
In this lesson, you will learn what Ansible vault is and how to use ansible vaults for Ansible operations.
UNDERSTANDING THE SUBJECT MATTER
What is Ansible Vault
From the word vault, Ansible vault is an ansible feature for safekeeping sensitive data such as usernames and passwords, etc.
In some of the previous lessons, we created some variable files that contain usernames and passwords. These data are sensitive and it is recommended to be protected.
With Ansible vault, these data can be protected.
it is not recommended that sensitive information like usernames and passwords should be in a playbook or a plain text file. It is best that such information is encrypted.
As we go on, we will see the step by step guide of how to do this in the ACTION TIME section below.
How do you secure secrets in Ansible?
secrets or sensitive data can be secured in Ansible by using the Ansible vault. The Ansible vault encrypts files and uses PyCrypto to encrypt and decrypt by default, thereby making files secure. Hence, Ansible vault is secured.
Ansible vault can encrypt files, variable files, arbitrary files, binary files, and single values inside of a YAML file.
File level encryption with Ansible is easy to use. It can be easily re keyed and pass-worded.
*To protect a file with Ansible vault, use the command,
# ansible-vault encrypt <file>For example, to encrypt the file with the name, database, use the command
# ansible-vault encrypt database*To create an encrypted file, use the command,
# ansible-vault create <file>For example, to create an encrypted file straightaway with the name database, use the command,
# ansible-vault create databaseHow Do I view Ansible Encrypted File
An Ansible encrypted file can be viewed.
To view an Ansible encrypted file, use the command,
# ansible-vault view <file>For example, to view an encrypted file with the name, database, use the command,
# ansible-vault view databaseHow Do I Edit Ansible Encrypted File
An Ansible encrypted file can be edited.
To edit an encrypted file that has been encrypted with the Ansible vault, use the command,
# ansible-vault edit <file>For example, to edit encrypted file with the name, database, use the command,
# ansible-vault edit databaseHow Do I re-key Ansible Encrypted File
The Ansible vault password of an encrypted file can be changed.
To change the password of an encrypted file, use the command,
# ansible-vault rekey <file>For example, to change the password of an encrypted file with the name, database, use the command,
# ansible-vault rekey databaseHow do I decrypt Ansible vault?
An Ansible encrypted file can be decrypted.
To decrypt an encrypted file, use the command,
# ansible-vault decrypt <file>For example, to decrypt an encrypted file with the name, database, use the command,
ansible-vault decrypt databaseHow do I bypass Ansible Vault password?
The Ansible vault password can be bypassed when running a playbook associated with encrypted files, that is, the password will not be prompted when trying to run Ansible operations.
To bypass Ansible vault password, follow the steps below.
*create a file and add the Ansible password in the file
# echo "password123" > confidential*run the playbook
# ansible-playbook <playbook> --vault-password-file=confidentialAs we go on, we are going to see how to bypass the vault password using examples in the ACTION TIME section below.
Having understood the subject matter and how to use the Ansible vault feature, let’s see the step by step guide of how to use Ansible vault with examples.
ACTION TIME
Step By Step Guide Of How To Use Ansible Vault In Linux
To create an encrypted variable file with the name, “confidential.yml”, and with the variable names “username” and “password”. Follow the steps below.
1. Create a variable file.
[lisa@drdev1 ~]$ mkdir -p host_vars/hqdev1.tekneed.com/[lisa@drdev1 ~]$ vim host_vars/hqdev1.tekneed.com/confidential.ymlusername: kehinde
password: kenny2. Encrypt the variable
*you can use tekneed as the password
[lisa@drdev1 ~]$ ansible-vault encrypt host_vars/hqdev1.tekneed.com/confidential.yml
New Vault password:
Confirm New Vault password:
Encryption successful
3. Verify it has been encrypted
[lisa@drdev1 ~]$ cat host_vars/hqdev1.tekneed.com/confidential.yml
$ANSIBLE_VAULT;1.1;AES256
646231313666653930363938373566643231303765653133356538396664
......NOTE: that this is one of the 22 ways variables can be declared.
Moving this example forward, create a playbook to use the variables with.
4. create a simple playbook file
[lisa@drdev1 ~]$ vim playbookone.yml---
- name: create users
hosts: hqdev1.tekneed.com
tasks:
- name: create users and password
user:
name: "{{ username }}"
password: "{{ password }}"
state: present5. Do a playbook syntax check
[lisa@drdev1 ~]$ ansible-playbook playbookone.yml --syntax-check
playbook: playbookone.yml
NOTE: If the variable file is in the same directory as the playbook, it will throw the error below.
[lisa@drdev1 ~]$ ansible-playbook playbookone.yml --syntax-check
ERROR! Attempting to decrypt but no vault secrets found[lisa@drdev1 ~]$ ansible-playbook playbookone.yml --syntax-check --ask-vault-pass
Vault password:
playbook: playbookone.yml
[lisa@drdev1 ~]$6. Run the playbook.
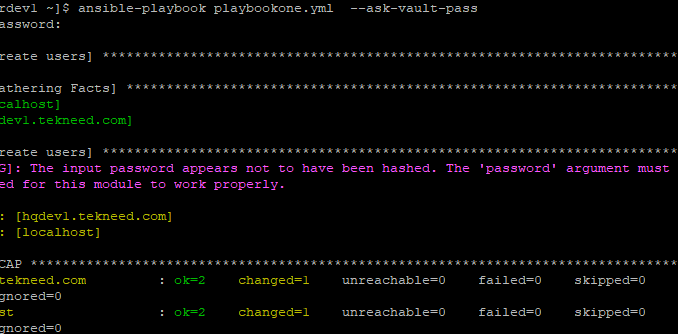
[lisa@drdev1 ~]$ ansible-playbook playbookone.yml --ask-vault-pass
Vault password:
PLAY [create users] *******************************************************************************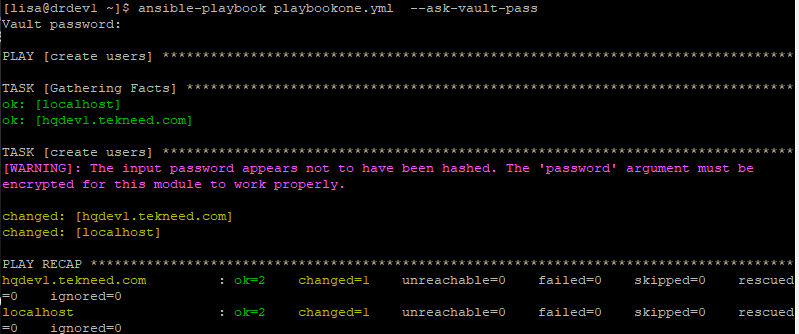
You can see the warning message saying the input password appears not to have been hashed, hence we need to encrypt the password in the variable file.
7. Encrypt the password in the variable file.
[root@hqdev1 ~]# openssl passwd -6
Password:
Verifying - Password:
$6$r8Bw3jZZfAR6qBBY$qro.c9fAHfnAwHxjQGcM3Bw6M8a06WTmXIFSFr/SztmKD.vaIVzZ27lVThd83xBNuAExK4.S.N.9KBuyGzuai.8. Edit the variable file and add the encrypted password instead of the plain text file.
[lisa@drdev1 ~]$ vim confidential.ymlusername: kehinde
password: $6$LbXZS8XEyg4alUZ.$a9wGeKuQoSWbYqG0P1VpzQsSgmgUfZ6V7u3Bt/qlQ0.dLTH76T2DELIOD3x8mZwHsLmIZ5s67LEkugLyZvFyu/9. Rerun the playbook
[lisa@drdev1 ~]$ ansible-playbook playbookone.yml --ask-vault-pass
Vault password:
PLAY [create users] ***********************************************************************You can see that the warning message is cleared.
*Another thing we can do is to run the playbook without prompting us for password. To do that,
10. create a password file
[lisa@drdev1 ~]$ vim confidentialtekneed[lisa@drdev1 ~]$ chmod 600 confidential11. Run the playbook again
[lisa@drdev1 ~]$ ansible-playbook playbookone.yml --vault-password-file=confidential
PLAY [create users] ************************************************************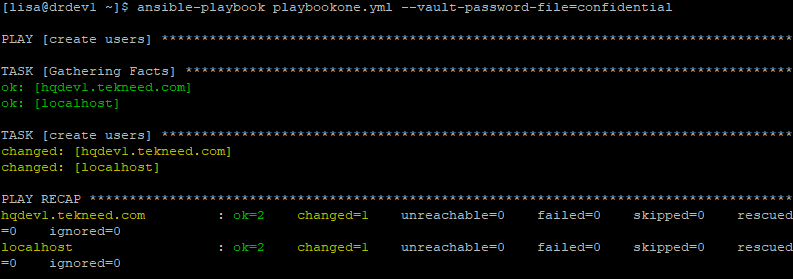
12. verify that the playbook ran successfully connecting to hqdev1.tekneed.com as the kenny user.
[lisa@drdev1 ~]$ ssh -o PreferredAuthentications=password kehinde@hqdev1.tekneed.com
kehinde@hqdev1.tekneed.com's password:
Managed by ansible
Activate the web console with: systemctl enable --now cockpit.socket
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
Last failed login: Thu Mar 25 17:24:24 WAT 2021 from 192.168.170.140 on ssh:notty
[kehinde@hqdev1 ~]$NOTE: The playbook can also be written as below:
---
- name: create users
hosts: hqdev1.tekneed.com
vars_files
- confidential.yml
tasks:
- name: create users and password
user:
name: "{{ username }}"
password: "{{ password }}"
state: presentIn this case, the variable has been declared in another method different from the first method above. The confidential.yml will may be referenced in the same directory as the playbook. Hence, you know you can declare variables however you wish, as far as it falls in the 22 different methods. Like I always say in this course, write your playbooks in a way you can easily understand and troubleshoot.
Class Activity
Just as we created a playbook of creating the username “kenny” above, create a playbook with the task of deleting the username “kenny”.
Make sure there is a separate variable file referencing the playbook. Also, make sure the variable files are encrypted.
If you like this article, you can support us by
1. sharing this article.
2. Buying the article writer a coffee (click here to buy a coffee)
3. Donating to push our project to the next level. (click here to donate)
If you need personal training, send an email to info@tekneed.com
Click Here To Watch Video On How To Manage Ansible Secretes With Ansible Vault
RHCE / EX294 Exam Practice Question On Managing Secrets With Ansible Vault
Your feedback is welcomed. If you love others, you will share with others
Leave a Reply