
Last updated: April 2022
In this lesson, you will learn how to manage users, groups, and authentication using Ansible with the use of the Ansible user module, Ansible group module, etc.
Contents
What Is User Module In Ansible
The Ansible user module is used for authentication management, such as, creating and managing user’s account and attributes.
Just like I have mentioned in one of the previous lessons, the “ansible-doc <module>” command can be used to get information about a module; the various options/argument of a module and how it is used.
Let’s see how the Ansible user module can be used with examples.
Ansible User Module With Examples – Creating User & Password
Let’s look at the following user attributes.
User Attributes
Username: jerry
user ID: 200
shell: bash
group: finance and wheelThe playbook written below can be used to create a user in hqsdev1.tekneed.com with the following attributes above.
[lisa@drsdev1 ~]$ vi ansible/user.ymlname: create administrative users
hosts: hqsdev1.tekneed.com
tasks:
- name: create admin user1
user:
name: jerry
uid: 200
shell: /bin/bash
groups: finance, wheel
append: yesLet’s understand these options.
name: The name option will create the username, jerry, in this case.
uid: The uid option will create the user ID, in this case, jerry’s user ID, which is 200 will be created
shell: The shell option will create the user’s shell, in this case, a bash shell.
groups: The group option is used to add a user to a group, in this case, jerry will be added to the finance and wheel group.
Don’t forget to use the append option just as we would use it when adding a user to a group without using Ansible. If you do not append the user in a group or use the append option, it means that the user will be removed from any group they belong to and will be added only to the group specified.
*Do a playbook syntax check.
[lisa@drsdev1 ~]$ cd ansible/[lisa@drsdev1 ansible]$ ansible-playbook user.yml --syntax-check
playbook: user.yml*Run the playbook
[lisa@drsdev1 ansible]$ ansible-playbook user.yml
PLAY [create users] ************************************************************
----------
Moving this example forward, the following task below can be used to generate an SSH key for the user, jerry.
............................
- name: create user jerry
user:
name: jerry
uid: 200
shell: /bin/bash
groups: finance,wheel
append: yes
generate_ssh_key: yes
ssh_key_file: .ssh/id_rsagenerate_ssh_key: This option is used to generate a SSH key for a user, in this case, SSH key will be generated for the user, jerry. This opiton will not overwrite an existing SSH key unless used with, force=yes.
ssh_key_file: This option is optionally used to specify the location where the SSH key will be generated.
Moving this exercise forward, the user, jerry should be able to perform his functions as a root user without prompting for a password.
NOTE that jerry is already in the wheel group and can perform his functions as a root user, however, he will still be prompted to enter his password to be able to perform his functions.
To do this without prompting for password, we need to edit the sudoer’s file. Better still, I’ll prefer to create a drop in file instead of editing the sudoer’s file.
Let’s create a drop in file in the sudoers.d directory for jerry to be able to fully perform his functions as a root user without prompting him to enter his password.
The Ansible task below can be used to do this.
......................
- name: create /etc/sudoers.d/jerry file
file:
path: /etc/sudoers.d/jerry
state: touch
- name: configure a pass-wordless authentication & execution for Jerry
lineinfile:
path: /etc/sudoers.d/jerry
line: "jerry ALL=(ALL) NOPASSWD: ALL"
state: presentThe first task (create /etc/sudoers.d/jerry file) will create an empty file with the name, /etc/sudoers.d/jerry with the use of the file module. We already learnt how to use Ansible file-related module in one our previous lessons.
The second task(configure a pass-wordless authentication & execution for jerry) will be used to populate the empty file created with the use of the lineinfile module.
Moving this exercise forward, logging into the managed host from the control node via SSH should be passwordless.
This means we need to install the SSH key on the control node to the managed node. This can be done using the authorized_key module.
The Ansible task below can be used to install the SSH key.
Using The Ansible authorized_key Module With Example
- name: install the SSH public key on managed host for jerry
authorized_key:
user: jerry
state: present
key: "{{ lookup('file', '/home/lisa/.ssh/id_rsa.pub') }}"authorized_key: This module will be used to install the SSH key.
user: This option means that the SSH key file will be installed for the user, jerry
state: This option is to specify if the key should be in the file or not. The default value is present.
key: This option is where the SSH key will be specified.
Just like I mentioned in one of the previous lessons, we have different types of Ansible plugins, modules itself is a type of Ansible plugin. In this case, the Ansible plugin, named the lookup plugin is used, and the name of the lookup plugin is file.
The file plugin will lookup the contents of the ‘id_rsa_pub’ file and use it to parse the operation to the managed node.
NOTE that the SSH key can be copied from the control node to the playbook, however, this makes the playbook untidy, and secondly, the SSH key is vulnerable because it is visible to anybody who has access to the playbook which is not a best practice. Another way of going about this is to create a variable.
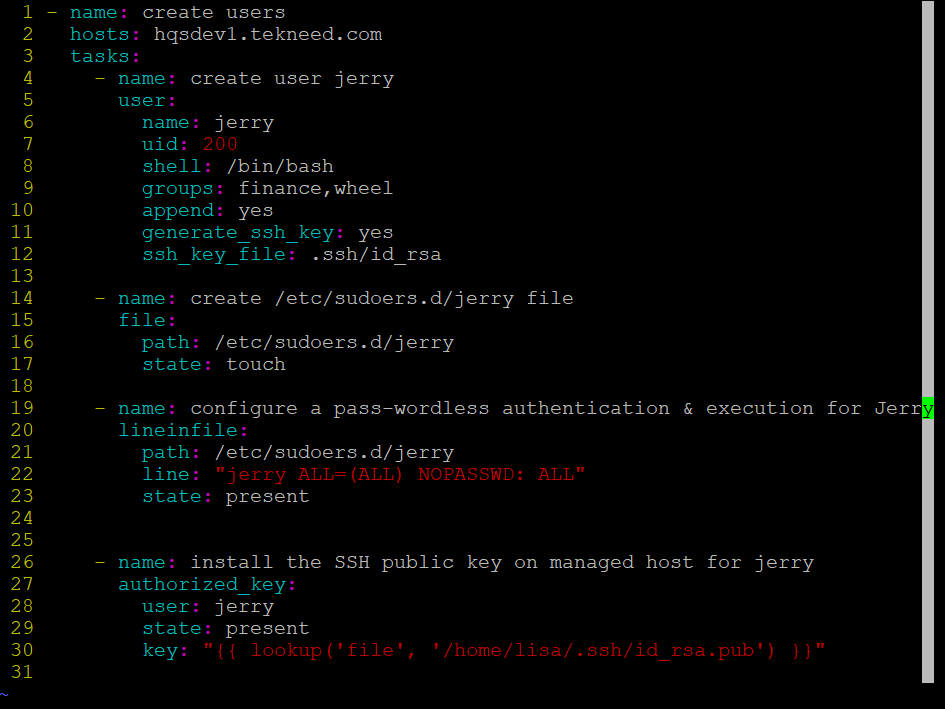
At the end, the playbook will look like this:
- name: create users
hosts: hqsdev1.tekneed.com
tasks:
- name: create user jerry
user:
name: jerry
uid: 200
shell: /bin/bash
groups: finance,wheel
append: yes
generate_ssh_key: yes
ssh_key_file: .ssh/id_rsa
- name: create /etc/sudoers.d/jerry file
file:
path: /etc/sudoers.d/jerry
state: touch
- name: configure a pass-wordless authentication & execution for Jerry
lineinfile:
path: /etc/sudoers.d/jerry
line: "jerry ALL=(ALL) NOPASSWD: ALL"
state: present
- name: install the SSH public key on managed host for jerry
authorized_key:
user: jerry
state: present
key: "{{ lookup('file', '/home/lisa/.ssh/id_rsa.pub') }}"
* Do a playbook syntax check
[lisa@drsdev1 ansible]$ ansible-playbook user.yml --syntax-check
playbook: user.yml
*Run the playbook
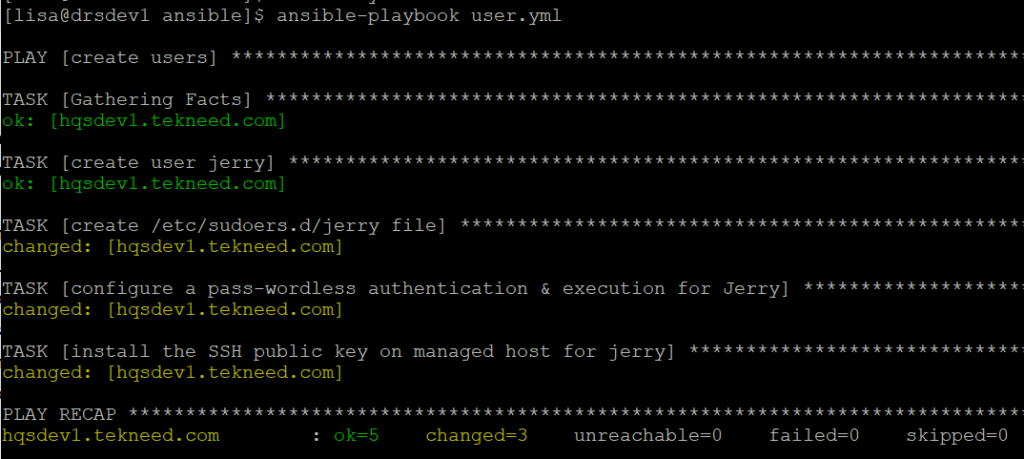
[lisa@drsdev1 ansible]$ ansible-playbook user.yml
PLAY [create users] ************************************************************
...........
*Verify the configuration
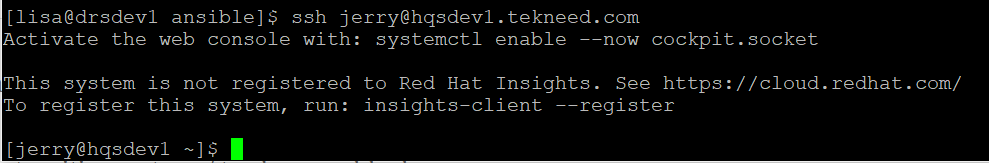
Try to login to the managed host as jerry to see if a password display is going to be prompted.
[lisa@drsdev1 ansible]$ ssh jerry@hqsdev1.tekneed.com
Activate the web console with: systemctl enable --now cockpit.socket
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
[jerry@hqsdev1 ~]$
Verify the user ID and the groups jerry belongs to
[jerry@hqsdev1 ~]$ id jerry
uid=200(jerry) gid=1003(jerry) groups=1003(jerry),10(wheel),1002(finance)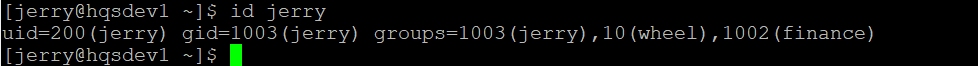
verify if the ssh key for jerry has been generated.
[jerry@hqsdev1 ~]$ ls .ssh/
authorized_keys id_rsa id_rsa.pubGoing forward, try to open another SSH connection outside the control node and try to login as the user, jerry. Can you? Absolutely not. And why is that? It is simply because we did not create password for the user, jerry.
Using Ansible To Create Password For Users
The option, “password”, with the “user” module can be used to create passwords for users. However, the passwords have to be encrypted on Linux machines and must be parsed using variables.
If one chooses not to use variables, the password must be in encrypted format as a value for the key/option, “password”.
Using the exercise above, to create a password for the user, jerry, a variable must be added and the password option must be used as it is in the playbook below.
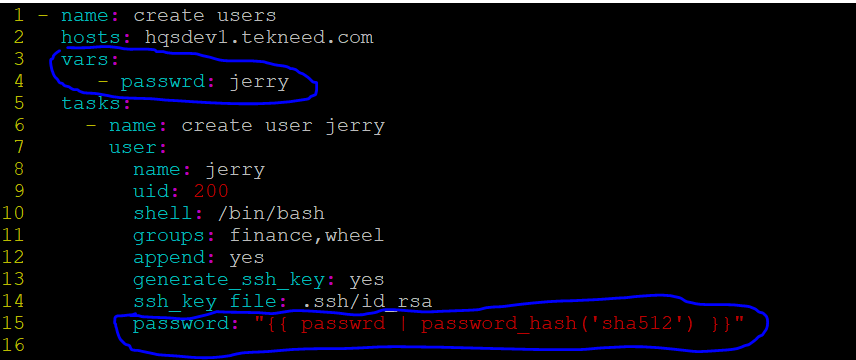
Here is what we have done, highlighted in blue . The variable, “passwrd” was created and the password used was jerry. The password will be encrypted in the sha512 format.
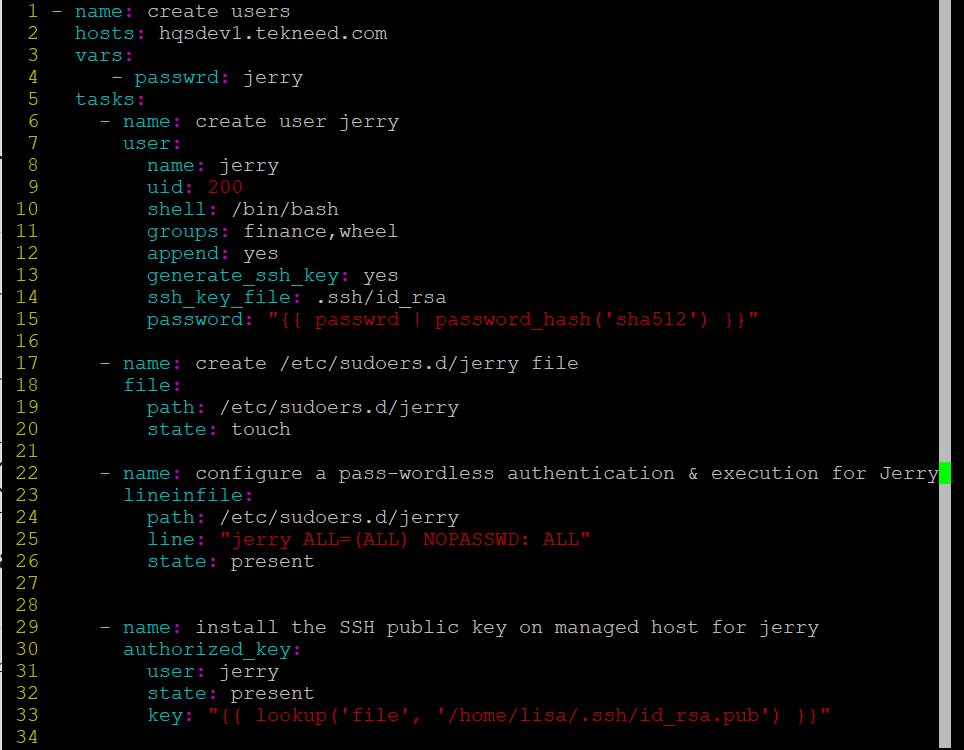
So, at the end of this exercise, the final playbook will look like this:
- name: create users
hosts: hqsdev1.tekneed.com
vars:
- passwrd: jerry
tasks:
- name: create user jerry
user:
name: jerry
uid: 200
shell: /bin/bash
groups: finance,wheel
append: yes
generate_ssh_key: yes
ssh_key_file: .ssh/id_rsa
password: "{{ passwrd | password_hash('sha512') }}"
- name: create /etc/sudoers.d/jerry file
file:
path: /etc/sudoers.d/jerry
state: touch
- name: configure a pass-wordless authentication & execution for Jerry
lineinfile:
path: /etc/sudoers.d/jerry
line: "jerry ALL=(ALL) NOPASSWD: ALL"
state: present
- name: install the SSH public key on managed host for jerry
authorized_key:
user: jerry
state: present
key: "{{ lookup('file', '/home/lisa/.ssh/id_rsa.pub') }}"
*Run the playbook
[lisa@drsdev1 ansible]$ ansible-playbook user.yml
PLAY [create users] ************************************************************
..............*Now, try logging in as the user, jerry, and with the password jerry. You should be able to login now.
Using Ansible group Module With Examples
Just as the Ansible user module is for users, the Ansible group module is used for authentication management, such as; to create and manage group account and attributes.
Just as we did some examples in the Ansibe user module section above, let’s see how the Ansible group module can also be used with examples
*create the playbook
[lisa@drsdev1 ansible]$ vi group.yml---
- name: create group
hosts: hqsdev1.tekneed.com
tasks:
- name: create the sales group or verify if its present
group:
name: sales
state: presentThis playbook above will use the group module to create a group with the name, sales and also make sure the group is present with the state option.
*Do a playbook syntax check.
[lisa@drsdev1 ansible]$ ansible-playbook group.yml --syntax-check
playbook: group.yml*Run the playbook
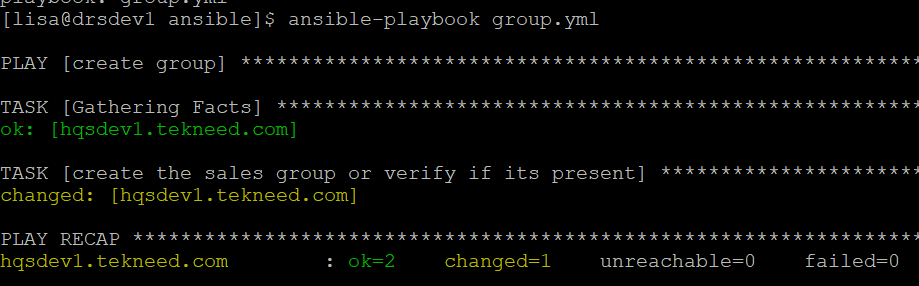
[lisa@drsdev1 ansible]$ ansible-playbook group.yml
PLAY [create group] ************************************************************
............
*Verify the configuration
[lisa@drsdev1 ansible]$ ansible hqsdev1.tekneed.com -a 'grep sales /etc/group'
hqsdev1.tekneed.com | CHANGED | rc=0 >>
sales:x:1006: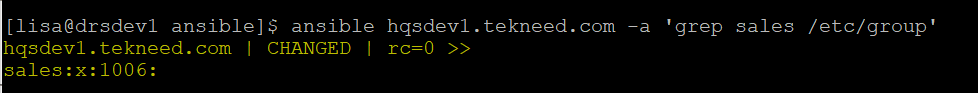
NOTE: The exam practice questions are very important because the questions they contain gives you hands-on, all-around experience. For example, other topics and this topic, creating users, involve you making use of loops, variables, handlers, roles, etc. These questions develop your brain and prepare you for the exam and also for the real production environment.
Watch Video On Using Ansible User Module & group Module With Examples
RHCE Exam Practice Questions On Using Ansible User Module & Ansible group Module
Your feedback is welcomed. If you love others, you will share with others
Leave a Reply