
Contents
In this tutorial, you will understand how logging in Linux is done and how you can manage logs in Linux.
UNDERSTANDING THE SUBJECT MATTER
Searching for logs on a Linux system, either for troubleshooting or for tracking down an event can be very interesting and painful as well depending on how logging is set up in an environment.
For modern days computing where there can be a large and complex environment, logging should be set up intelligently to make work and life easier.
Before we look at how we can set up logging, let us understand how logging works in Linux.
In modern Linux operating systems, two services/daemons manage logging. They are journald and rsyslog. These two services are responsible for handling logging activities on a system.
When a Linux system is powered on, the first service that is started is systemd. Systemd becomes the parent process (service) to other services on the system. Systemd is responsible for starting other services.
More so, systemd, with the use of the systemctl tool can restart and stop other services after they have been started at boot time.
Systemd keeps track of all these activities as they are being performed. The reason why you get to see logs after starting or restarting services on the system with the systemctl tool.
Let’s have a look at some of these logs.
[root@HQEBPRD ~]# systemctl status sshd
● sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2020-04-06 10:27:03 WAT; 5h 0min ago
Docs: man:sshd(8)
man:sshd_config(5)
Main PID: 1252 (sshd)
Tasks: 1 (limit: 11337)
Memory: 15.9M
CGroup: /system.slice/sshd.service
└─1252 /usr/sbin/sshd -D -oCiphers=aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr,aes256-cbc,aes128-gcm@openssh.com,aes128-ctr,aes128-cbc ->
Apr 06 10:27:02 HQEBPRD systemd[1]: Starting OpenSSH server daemon...
Apr 06 10:27:03 HQEBPRD sshd[1252]: Server listening on 0.0.0.0 port 2019.
Apr 06 10:27:03 HQEBPRD sshd[1252]: Server listening on :: port 2019.
Apr 06 10:27:03 HQEBPRD systemd[1]: Started OpenSSH server daemon.
Apr 06 10:59:24 HQEBPRD sshd[3514]: Accepted password for root from 192.168.170.1 port 60283 ssh2
Apr 06 10:59:24 HQEBPRD sshd[3514]: pam_unix(sshd:session): session opened for user root by (uid=0)
Apr 06 15:20:31 HQEBPRD sshd[5693]: Accepted password for root from 192.168.170.1 port 62936 ssh2
Apr 06 15:20:31 HQEBPRD sshd[5693]: pam_unix(sshd:session): session opened for user root by (uid=0)
lines 1-19/19 (END)
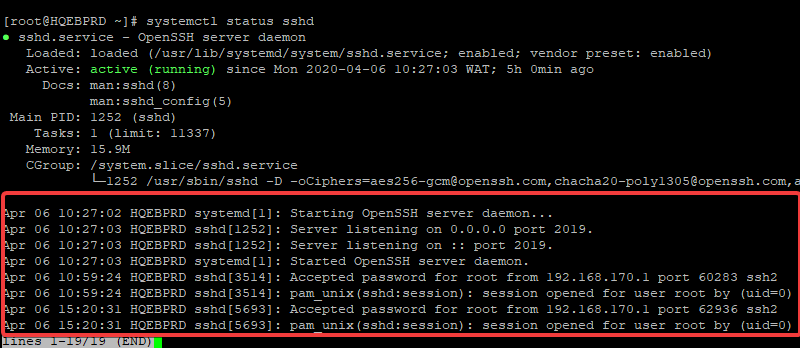
You can see the logs in the screenshot showing the date and time of when the activities as seen above took place.
These are the logs that systemd keeps, even while booting, systemd will forward them as a binary file to journald/journal. Journald will then hold the logs from systemd. Hence, when a user needs to get a log, the user can get the logs from the journal with the use of the journalctl tool.
The systemctl tool and the journalctl tool can both be used to get logs from journald’s binary file. When you use the systemctl tool, it fetches logs from journald, when you use the journactl tool, it also fetches logs from journald.
Another example is this.
[root@HQEBPRD etc]# systemctl restart sshd
Job for sshd.service failed because the control process exited with error code.
See "systemctl status sshd.service" and "journalctl -xe" for details.
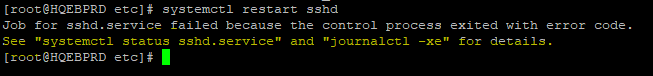
you can see that from the screenshot, to know what the issue may be, you will need to use the command “systemctl status sshd.service” and “journalctl -xe” for details. We will look at different ways with examples of how we can use the journalctl tool in the “ACTION TIME” section.
To check the journald service status, use the command,
[root@HQEBPRD log]# systemctl status systemd-journald
● systemd-journald.service - Journal Service
Loaded: loaded (/usr/lib/systemd/system/systemd-journald.service; static; vendor preset: disabled)
Active: active (running) since Wed 2020-04-08 23:17:00 WAT; 1 day 18h ago
Docs: man:systemd-journald.service(8)
man:journald.conf(5)
Main PID: 784 (systemd-journal)
Status: "Processing requests..."
Tasks: 1 (limit: 11337)
Memory: 2.8M
CGroup: /system.slice/systemd-journald.service
└─784 /usr/lib/systemd/systemd-journald
Apr 08 23:17:00 HQEBPRD systemd-journald[784]: Journal started
Apr 08 23:17:00 HQEBPRD systemd-journald[784]: Runtime journal (/run/log/journal/a42eb5b5bacc41df93f034>
Apr 08 23:17:00 HQEBPRD systemd-journald[784]: Runtime journal (/run/log/journal/a42eb5b5bacc41df93f034>
lines 1-15/15 (END)
The journal is not persistent by default. However, we can make it persistent. Click here to learn more about journald.
Moving forward, let us look at how rsyslog works
rsyslog service was the classic way of managing logs on the Linux system before the introduction of journald. On many systems, both services are still used till today to manage log files.
Just as journald, rsyslog utility also gather log files from different services, sorts them and put them in different paths in the “/var/log” directory.
If you notice, on RHEL 7&8, systemd-journald handles the the startup logs from the boot process, forwards the logs to rsyslog for further processing, rsyslog then sorts out the logs and put them in the “/var/log” directory by their types. rsyslog is also able to handle the current logs on the system very well.
Let’s have a look at the “/var/log” directory.
[root@HQEBPRD etc]# cd /var/log
[root@HQEBPRD log]# ls
anaconda hawkey.log-20200315 secure-20200405
audit hawkey.log-20200322 speech-dispatcher
boot.log hawkey.log-20200329 spooler
boot.log-20200324 hawkey.log-20200405 spooler-20200315
boot.log-20200328 insights-client spooler-20200322
boot.log-20200329 lastlog spooler-20200329
boot.log-20200401 libvirt spooler-20200405
boot.log-20200404 maillog sssd
boot.log-20200405 maillog-20200315 swtpm
boot.log-20200406 maillog-20200322 tuned
btmp maillog-20200329 vmware-network.1.log
btmp-20200401 maillog-20200405 vmware-network.2.log
chrony messages vmware-network.3.log
cron messages-20200315 vmware-network.4.log
cron-20200315 messages-20200322 vmware-network.5.log
cron-20200322 messages-20200329 vmware-network.6.log
cron-20200329 messages-20200405 vmware-network.7.log
cron-20200405 private vmware-network.8.log
cups qemu-ga vmware-network.9.log
dnf.librepo.log README vmware-network.log
dnf.log rhsm vmware-vgauthsvc.log.0
dnf.rpm.log samba vmware-vmsvc.log
firewalld secure vmware-vmusr.log
gdm secure-20200315 wtmp
glusterfs secure-20200322 Xorg.9.log
hawkey.log secure-20200329
[root@HQEBPRD log]#
you can see the different log files being sorted out in this directory, your output may be different depending on the services and the version of your Linux operating system. I am using a RHEL 8.1 for this subject matter.
Let’ analyze some of the important files in this directory.
1. Messages file
The “/var/log/messages” file contains all syslog messages. I.e, all logs related to the entire system, this file will capture all the system activities. In some distributions like Debian, the path is “/var/log/syslog”. Other messages files are as a result of log rotation.
2. Secure file
The “/var/log/secure” file contains all logs that are related to security and authentication, both the successful and the unsuccessful logins and errors. In some distributions like Debian, the path is “/var/log/auth.log”. Other secure files are as a result of log rotation.
3. Maillog file
The “/var/log/maillog” file contains all mail logs, including errors related to mail services. In some distributions, the path is “/var/log/mail.log”. Other maillog files are as a result of log rotation.
4. Boot.log file
The “/var/log/boot.log file contains all logs related to the booting of the system. Other boot.log files are as a result of log rotation.
5. Cron file
The “/var/log/cron” file contains all logs related to cron jobs, inclusive of errors of failed cron jobs. Other cron files are as a result of log rotation.
6. Wtmp file
The “/var/log/wtmp” file contains all related login and logout logs.
An example of a command you can use to query the wtmp file is,
[root@HQEBPRD ~]# last reboot
reboot system boot 4.18.0-147.el8.x Wed Apr 8 23:16 still running
wtmp begins Wed Apr 8 23:16:57 2020
[root@HQEBPRD ~]#
Going forward, some services (applications) may decide to write their log files via rsyslog service in the “/var/log” directory or via journald service as a binary file. Some services may even decide to write their log files in a different location entirely.
It all depends on how the services (applications) are developed to write their log files. It is the job of a user or an administrator to always check these different locations to get logs and it can be tiring sometimes.
However, for easier management of logs, one can configure all logs to either go through rsyslog or via journald. More so, one can configure all logs to be logged to a centralized server thereby making log management easier. I will write about how these can be done in another article.
You should also know that there are other utilities that can be used to configure and manage logging as well. They are the likes of logwatch, logcheck, ELK stack, solarwinds log & event manager, etc. I will also write about how some of these applications can be configured and used in another article.
To check the rsyslog service status, use the command,
[root@HQEBPRD ~]# systemctl status rsyslog
● rsyslog.service - System Logging Service
Loaded: loaded (/usr/lib/systemd/system/rsyslog.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2020-04-08 23:17:44 WAT; 2 days ago
Docs: man:rsyslogd(8)
http://www.rsyslog.com/doc/
Main PID: 1829 (rsyslogd)
Tasks: 3 (limit: 11337)
Memory: 3.8M
CGroup: /system.slice/rsyslog.service
└─1829 /usr/sbin/rsyslogd -n
Apr 08 23:17:18 HQEBPRD systemd[1]: Starting System Logging Service...
Apr 08 23:17:44 HQEBPRD rsyslogd[1829]: environment variable TZ is not set, auto correcting this to TZ=>
Apr 08 23:17:44 HQEBPRD systemd[1]: Started System Logging Service.
Apr 08 23:17:44 HQEBPRD rsyslogd[1829]: [origin software="rsyslogd" swVersion="8.37.0-13.el8" x-pid="1>
Apr 08 23:17:44 HQEBPRD rsyslogd[1829]: imjournal: No statefile exists, /var/lib/rsyslog/imjournal.stat>
lines 1-16/16 (END)
Having understood how journald and rsyslog works, let’s look at some journactl commands that can be used to query logs from the journald binary file.
ACTION TIME
How To View Logs With journalctl Utility In Linux
How To View All Logs With Journalctl
To view all logs with journalctl, use the command,
[root@HQEBPRD ~]# journalctl
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 16:27:58 WAT. --
Apr 08 23:16:53 HQEBPRD kernel: Linux version 4.18.0-147.el8.x86_64 (mockbuild@x86-vm-09.build.eng.bos.>
Apr 08 23:16:53 HQEBPRD kernel: Command line: BOOT_IMAGE=(hd0,msdos1)/vmlinuz-4.18.0-147.el8.x86_64 roo>
Apr 08 23:16:53 HQEBPRD kernel: Disabled fast string operations
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x001: 'x87 floating point registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x002: 'SSE registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x004: 'AVX registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: xstate_offset[2]: 576, xstate_sizes[2]: 256
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Enabled xstate features 0x7, context size is 832 bytes, using >
Apr 08 23:16:53 HQEBPRD kernel: BIOS-provided physical RAM map:
Apr 08 23:16:53 HQEBPRD kernel: BIOS-e820: [mem 0x0000000000000000-BIOS-e820: [mem 0x00000000fee00000-
...............................................................How To View The Realtime Logs With journalctl
To view real-time logs with journalctl, use the command,
[root@HQEBPRD ~]# journalctl -f
-- Logs begin at Wed 2020-04-08 23:16:53 WAT. --
Apr 10 23:22:52 HQEBPRD systemd[1]: Starting Cleanup of Temporary Directories...
Apr 10 23:22:52 HQEBPRD systemd-tmpfiles[55566]: [/usr/lib/tmpfiles.d/mdadm.conf:1] Line references path below legacy directory /var/run/, updating /var/run/mdadm → /run/mdadm; please update the tmpfiles.d/ drop-in file accordingly.
Apr 10 23:22:52 HQEBPRD systemd-tmpfiles[55566]:
...........................................
How To Display The Logs From The Newest To The Oldest Logs With journalctl
Logs usually are displayed from the oldest to the newest, to reverse the order, use the command,
[root@HQEBPRD ~]# journalctl -r
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 23:36:56 WAT. --
Apr 10 23:36:56 HQEBPRD systemd[1]: Started dnf makecache.
Apr 10 23:36:56 HQEBPRD dnf[55737]: Metadata cache refreshed recently.
Apr 10 23:36:52 HQEBPRD dnf[55737]: Updating Subscription Management repositories.
Apr 10 23:36:52 HQEBPRD systemd[1]: Starting dnf makecache...
Apr 10 23:33:01 HQEBPRD systemd[1]: Started Network Manager Script Dispatcher Service.
.........................................How To View Logs For The Last Boot With journactl
To view the logs for the last boot of the system, use the command,
[root@HQEBPRD ~]# journalctl -b
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 16:27:58 WAT. --
Apr 08 23:16:53 HQEBPRD kernel: Linux version 4.18.0-147.el8.x86_64 (mockbuild@x86-vm-09.build.eng.bos.>
Apr 08 23:16:53 HQEBPRD kernel: Command line: BOOT_IMAGE=(hd0,msdos1)/vmlinuz-4.18.0-147.el8.x86_64 roo>
Apr 08 23:16:53 HQEBPRD kernel: Disabled fast string operations
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x001: 'x87 floating point registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x002: 'SSE registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x004:
Apr 08 23:16:53 HQEBPRD kernel: BIOS-provided physical RAM map:
.................................................................
How To View Logs Within A Time Range with journalctl
- To view logs from the previous day, use the command,
[root@HQEBPRD ~]# journalctl --since=yesterday
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 16:27:58 WAT. --
Apr 09 00:00:00 HQEBPRD systemd[1]: Starting update of the root trust anchor for DNSSEC validation in u>
Apr 09 00:00:01 HQEBPRD systemd[1]: Started update of the root trust anchor for DNSSEC validation in un>
Apr 09 00:01:01 HQEBPRD CROND[6413]: (root) CMD (run-parts /etc/cron.hourly)
Apr 09 00:01:01 HQEBPRD run-parts[6416]: (/etc/cron.hourly) starting 0anacron
Apr 09 00:01:01 HQEBPRD anacron[6422]: Anacron started on 2020-04-09
Apr 09 00:01:01 HQEBPRD run-parts[6424]: (/etc/cron.hourly) finished 0anacron
Apr 09 00:01:01 HQEBPRD anacron[6422]: Will run job `cron.daily' in 41 min.
Apr 09 00:01:01 HQEBPRD anacron[6422]: Will run job `cron.weekly' in 61 min.
Apr 09 00:01:01 HQEBPRD anacron[6422]: Will run job `cron.monthly' in 81 min.
........................................
- To view logs from today, use the command,
[root@HQEBPRD ~]# journalctl --since today
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 23:39:09 WAT. --
Apr 10 00:00:30 HQEBPRD systemd[1]: Starting update of the root trust anchor for DNSSEC validation in unbound...
Apr 10 00:01:01 HQEBPRD CROND[50517]: (root) CMD (run-parts /etc/cron.hourly)
Apr 10 00:01:01 HQEBPRD run-parts[50520]: (/etc/cron.hourly) starting 0anacron
Apr 10 00:01:01 HQEBPRD anacron[50526]: Anacron started on 2020-04-10
Apr 10 00:01:01 HQEBPRD run-parts[50528]: (/etc/cron.hourly) finished 0anacron
...........- To view logs since one hour ago, use the command,
[root@HQEBPRD ~]# journalctl --since "1 hour ago"
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Sat 2020-04-11 00:01:01 WAT. --
Apr 10 23:06:31 HQEBPRD NetworkManager[1231]: <info> [1586556391.5989] dhcp4 (ens33): state changed bound -> bound
Apr 10 23:06:31 HQEBPRD dbus-daemon[1049]: [system] Activating via systemd: service name='org.freedesktop.nm_dispatcher' unit='dbus-org.freedesktop.nm-dispatcher.servi>
Apr 10 23:06:31 HQEBPRD systemd[1]: Starting Network Manager Script Dispatcher Service...
Apr 10 23:06:31 HQEBPRD dbus-daemon[1049]: [system] Successfully activated service 'org.freedesktop.nm_dispatcher'
Apr 10 23:06:31 HQEBPRD systemd[1]: Started Network Manager Script Dispatcher Service.
..........- To view logs between 2pm and 8pm on 3rd of November, 2020 for ssh service, use the command,
[root@DRDEV1 ~]# journalctl -u sshd.service --since "2020-11-03 14:00" --until "2020-11-03 20:00"
-- Logs begin at Tue 2020-11-03 12:36:44 GMT, end at Sat 2020-11-07 14:33:09 GMT. --
Nov 03 15:23:12 DRDEV1 sshd[4945]: Accepted password for root from 192.168.170.1 port 56482 ssh2
Nov 03 15:23:12 DRDEV1 sshd[4945]: pam_unix(sshd:session): session opened for user root by (uid=0)
How To View The Kernel Messages With journalctl
[root@HQEBPRD ~]# journalctl -k
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 23:53:27 WAT. --
Apr 08 23:16:53 HQEBPRD kernel: Linux version 4.18.0-147.el8.x86_64 (mockbuild@x86-vm-09.build.eng.bos.redhat.com) (gcc version 8.3.1 20190507 (Red Hat 8.3.1-4) (GCC))>
Apr 08 23:16:53 HQEBPRD kernel: Command line: BOOT_IMAGE=(hd0,msdos1)/vmlinuz-4.18.0-147.el8.x86_64 root=/dev/mapper/rhel-root ro crashkernel=auto resume=/dev/mapper/r>
Apr 08 23:16:53 HQEBPRD kernel: Disabled fast string operations
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x001: 'x87 floating point registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x002: 'SSE registers'
Apr 08 23:16:53 HQEBPRD kernel: x86/fpu: Supporting XSAVE feature 0x004: 'AVX registers'
Apr 08 23:16:53 HQEBPRD kernel: BIOS-provided physical RAM map:
Apr 08 23:16:53 HQEBPRD kernel: BIOS-e820: [mem 0x0000000000000000-
.................How To View The Logs For a Specific Service or a Unit With journalctl
To view the logs for a specific service or unit, use the command
# journalctl -u <service-name>For example, to view the logs for the sshd service, use the command,
[root@HQEBPRD ~]# journalctl -u sshd.service
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 16:27:58 WAT. --
Apr 08 23:17:12 HQEBPRD systemd[1]: Starting OpenSSH server daemon...
Apr 08 23:17:12 HQEBPRD sshd[1253]: Server listening on 0.0.0.0 port 22.
Apr 08 23:17:12 HQEBPRD sshd[1253]: Server listening on :: port 22.
Apr 08 23:17:12 HQEBPRD systemd[1]: Started OpenSSH server daemon.
Apr 09 00:46:11 HQEBPRD sshd[8514]: Accepted password for root from 192.168.170.1 port 55882 ssh2
Apr 09 00:46:11 HQEBPRD sshd[8514]: pam_unix(sshd:session): session opened for user root by (uid=0)
Apr 10 16:27:58 HQEBPRD sshd[52913]: Accepted password for root from 192.168.170.1 port 60233 ssh2
Apr 10 16:27:58 HQEBPRD sshd[52913]: pam_unix(sshd:session): session opened for user root by (uid=0)
lines 1-18/18 (END)
To get more information on the sshd service, use the command,
[root@HQEBPRD ~]# journalctl -u sshd -o verbose
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Fri 2020-04-10 16:40:52 WAT. --
Wed 2020-04-08 23:17:12.596684 WAT [s=7ddb25e1f933421f87907dc444ee9561;i=795;b=be3ca02b6ade4eb2872ee769>
_BOOT_ID=be3ca02b6ade4eb2872ee7697a401338
_MACHINE_ID=a42eb5b5bacc41df93f034f80848713a
_HOSTNAME=HQEBPRD
PRIORITY=6
SYSLOG_FACILITY=3
SYSLOG_IDENTIFIER=systemd
_UID=0
_GID=0
_CAP_EFFECTIVE=3fffffffff
_TRANSPORT=journal
_PID=1
_COMM=systemd
_EXE=/usr/lib/systemd/systemd
_SYSTEMD_CGROUP=/init.scope
_SYSTEMD_UNIT=init.scope
_SYSTEMD_SLICE=-.slice
CODE_FILE=../src/core/unit.c
CODE_LINE=1683
CODE_FUNC=unit_status_log_starting_stopping_reloading
MESSAGE_ID=7d4958e842da4a758f6c1cdc7b36dcc5
_CMDLINE=/usr/lib/systemd/systemd --switched-root --system --deserialize 17
_SELINUX_CONTEXT=system_u:system_r:init_t:s0
MESSAGE=Starting OpenSSH server daemon...
UNIT=sshd.service
lines 1-26
How To View The Logs Of a Particular Priority With journalctl
- To view the logs of a particular facility, use the command,
[root@DRDEV1 ~]# journalctl -u sshd.service --since "2020-11-03 14:00" --until "2020-11-03 20:00" -p info
-- Logs begin at Tue 2020-11-03 12:36:44 GMT, end at Sat 2020-11-07 14:46:37 GMT. --
Nov 03 15:23:12 DRDEV1 sshd[4945]: Accepted password for root from 192.168.170.1 port 56482 ssh2
Nov 03 15:23:12 DRDEV1 sshd[4945]: pam_unix(sshd:session): session opened for user root by (uid=0)
[root@DRDEV1 ~]# journalctl -r -p err
-- Logs begin at Tue 2020-11-03 12:36:44 GMT, end at Sat 2020-11-07 14:46:37 GMT. --
Nov 07 14:46:37 DRDEV1 systemd[1]: Timed out waiting for device dev-disk-by\x2duuid-e0e0c163\x2d507e\x2d4059\x2d8f49\x>
............[root@DRDEV1 ~]# journalctl -r -n 5
-- Logs begin at Tue 2020-11-03 12:36:44 GMT, end at Sat 2020-11-07 14:46:37 GMT. --
Nov 07 14:46:37 DRDEV1 systemd[1]: dev-disk-by\x2duuid-e0e0c163\x2d507e\x2d4059\x2d8f49\x2d6ee80930649c.device: Job de>
Nov 07 14:45:07 DRDEV1 systemd[1]: Started Network Manager Script Dispatcher Service.
Nov 07 14:45:07 DRDEV1 dbus-daemon[1044]: [system] Successfully activated service 'org.freedesktop.nm_dispatcher'
Nov 07 14:45:07 DRDEV1 systemd[1]: Starting Network Manager Script Dispatcher Service...
Nov 07 14:45:07 DRDEV1 dbus-daemon[1044]: [system] Activating via systemd: service name='org.freedesktop.nm_dispatcher>
lines 1-6/6 (END)
How To View The Logs Generated By A User With journalctl
To view the logs generated by a user, use the command,
# journalctl _UID=<user-ID>For example, to see the logs generated by user ID 1000, use the command,
[root@HQEBPRD ~]# journalctl _UID=1000
-- Logs begin at Wed 2020-04-08 23:16:53 WAT, end at Sat 2020-04-11 00:03:02 WAT. --
Apr 09 00:37:52 HQEBPRD systemd[7203]: Starting D-Bus User Message Bus Socket.
Apr 09 00:37:52 HQEBPRD systemd[7203]: Reached target Paths.
Apr 09 00:37:52 HQEBPRD systemd[7203]: Started Mark boot as successful after the user session has run 2>
Apr 09 00:37:52 HQEBPRD systemd[7203]: Listening on Multimedia System.
Apr 09 00:37:52 HQEBPRD systemd[7203]: Listening on Sound System.
Apr 09 00:37:52 HQEBPRD systemd[7203]: Reached target Timers.
Apr 09 00:37:52 HQEBPRD systemd[7203]: Listening on D-Bus User Message Bus Socket.
.......In conclusion, you can check the manual page for journalctl to be able to effectively use it in your environment.
Your feedback is welcomed. If you love others, you will share with others
Leave a Reply