Last updated: November 2025

In the digital world, where cyber threats are everywhere and data breaches are costly, protecting your network is non-negotiable. One of the most effective lines of defense is installing a firewall. Whether you’re setting up a firewall for personal use, a small business, or enterprise-level security, knowing how to properly install and configure one is critical.
Here’s the problem: many people hear firewall they immediately get scared. They think firewalls are too technical or reserved for cybersecurity professionals. This guide breaks that myth. We’ll walk you through the process step-by-step, using practical tips so that even a beginner can get started.
This guide covers:
Table of Contents
- Introduction
- What is a firewall?
- Why Do You Need a Firewall?
- Types of Firewalls
- Pre-Installation Checklist
- Installing a Software Firewall (Windows Example)
- Installing a Hardware Firewall (Generic Steps)
- Installing pfSense (Advanced Users)
- Firewall Configuration Best Practices
- Troubleshooting Common Issues
- Common Mistakes to Avoid
- Conclusion
- Citations
What Is a Firewall?
A firewall is a security barrier that separates your internal network from external threats. It acts like a fence with a gatekeeper. Firewall gets their name from actual firewalls found in buildings that act as a barrier to prevent fire from going over either side of the wall. In the same vein, firewalls in cybersecurity monitor and filter incoming and outgoing data based on preset security rules.
You can think of a firewall as a security guard at a private building:
- Allowed visitors get access (safe traffic).
- Suspicious visitors are questioned or blocked (malicious traffic).
Firewalls can be hardware devices, software applications, or cloud services. They inspect data packets and decide whether to allow, block, or flag them for review.
Main Functions:
- Traffic Filtering: Controls which data packets pass through.
- Threat Prevention: Stops malware and hacking attempts.
- Access Control: Restricts users or devices from unsafe areas.
- Monitoring & Logging: Records activity for auditing and forensic analysis.
Without a firewall, malicious actors could gain direct access to your network and install malware, steal data, or even use your computer in larger attacks. Which leads us to why you need a firewall
Why You Need a Firewall
The risks of going without a firewall are significant.
Imagine your office has 10 computers connected to the same Wi-Fi.
- One employee downloads free “video converter” software that secretly has a worm.
- Overnight, the worm spreads to all other computers, slowing everything down.
- Printers stop working, files take forever to open, and your network crashes every few minutes.
- IT discovers every computer is now running the same malicious program, sending spam emails from your company email addresses.
This is how the ILOVEYOU worm (2000) and WannaCry (2017) spread worldwide in hours. That is just one out of many ways you can risk your data and your company’s data without installing a firewall. Other risks include
- A hacker scans your open ports and installs ransomware.
- A worm spreads across your network, consuming resources.
- Sensitive customer data was stolen because there was no traffic monitoring.
Firewalls help to
- Block unauthorized access.
- Stop malicious code from spreading.
- Protect sensitive data and maintain compliance (GDPR, HIPAA).
- Maintain network performance by filtering unnecessary traffic.
According to IBM’s 2023 Cost of a Data Breach Report, the average global cost of a data breach is $4.45 million.. Imagine that much loss because we can’t protect our data well enoughA properly configured firewall can prevent many breaches before they even start.
Types of Firewalls
Before you start the installation process, you need to know the types of firewalls available and which is best applicable to you
Types of Firewalls
1. Software Firewalls
- Works on individual computers, laptops, or mobile devices.
- Best for: Personal use or protecting a single device.
- Examples:
- Windows Defender Firewall (comes pre-installed on Windows).
- ZoneAlarm (free & paid options).
- Comodo Firewall (advanced users).
2. Hardware Firewalls
- They run on a separate, physical device.
- Best for: Businesses, offices, or homes with multiple users and devices.
- Examples: Often built into Wi-Fi routers or available as standalone devices like Fortinet, SonicWall, or Cisco ASA.
3. Cloud-Based Firewalls (Firewall-as-a-Service)
- Where they run: On the internet (in the cloud), managed by a security provider.
- Best for: Companies with remote workers or many offices in different places.
- Examples: Cisco Umbrella, Zscaler.
4. Next-Generation Firewalls (NGFWs)
- Where they run: On hardware devices, but with advanced software.
- What they do:
- Inspect traffic deeply (not just the surface).
- Block hacking attempts automatically.
- Recognize which apps are using your network.
- Examples: Palo Alto NGFW, FortiGate NGFW.
Checklist before installation
Before installing any firewall, do these 5 things to avoid mistakes:
- Define Your Goals:
- Do you want to block certain websites?
- Limit internet use during work hours?
- Keep hackers from scanning your devices?
- Know Your Devices:
- Make a list of computers, printers, smart TVs, or cameras you want to protect.
- Understand Your Network Layout:
- Know your router IP address, device IP ranges, and where your internet comes in.
- Choose the Right Firewall Type:
- Software firewall for personal use.
- Hardware firewall for home/office.
- Cloud firewall for remote teams.
- Back Up Your Settings:
- Save your router configuration and important files in case something goes wrong.
Installing a Software Firewall (Windows)
Most Windows users already have Windows Defender Firewall installed. Here’s how to check and configure it:
Step 1: Open Windows Firewall
- Go to Control Panel → System and Security → Windows Defender Firewall.
- Click Turn Windows Defender Firewall on or off.
Step 2: Turn It On
- Make sure it is ON for both private and public networks.
- Click OK to save.
Step 3: Create Rules
- Go to Advanced Settings → Inbound Rules → New Rule.
- Choose what you want to control (e.g., a program or port).
- Example: Block TCP port 80 to stop certain web traffic.
Step 4: Test and Monitor
- Use Command Prompt:
ping google.com→ Check internet connection.netstat -a→ See active connections.
Installing a Hardware Firewall (General Steps)
Installing a Cisco firewall (such as the ASA or Firepower series) involves physical setup, initial configuration via a console connection, and then more detailed configuration using either the Command Line Interface (CLI) or the graphical Cisco Adaptive Security Device Manager (ASDM).
Phase 1: Physical Installation
- Unpack and Inspect the device and ensure all necessary cables (power, console, Ethernet) are present and intact.
- Mount the Firewall in its intended location (e.g., a server rack), ensuring proper power supply considerations like grounding and an uninterruptible power source if possible.
- Connect Network Cables:
- Connect the outside interface (e.g., GigabitEthernet 1/1) to your WAN modem or router (internet source).
- Connect the inside interface (e.g., GigabitEthernet 1/2) to your internal network switch or computer.
- Connect any other interfaces (e.g., DMZ) to their respective network segments.
- Connect a Console Cable from the firewall’s console port (RJ-45 or USB) to your management computer’s serial or USB port. This provides initial direct access.
- Power On the device. The power usually turns on automatically when the power cable is attached and connected to an electrical outlet; some models may have a power switch on the rear.
- Verify LEDs: Check that the Power and Status LEDs turn solid green, indicating the device is powered on and has passed diagnostics.
How to set up your firewall in 6 steps – Cisco
How to set up your firewall in 6 steps · Step 1: Secure your firewall (Seems redundant, we know.) · Step 2: Architect firewall zon…

Cisco Systems

How to Configure a Firewall in Cisco Switch? – GeeksforGeeks
Jul 23, 2025 — Beginning in global configuration mode, carry out the following steps to set up firewall inspection rules for all T…

GeeksforGeeks
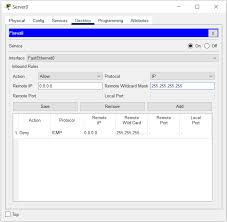
Phase 2: Initial Configuration (CLI Access)
- Launch Terminal Software (e.g., PuTTY) on your computer and configure a serial connection to the correct COM port using the default settings: 9600 baud rate, 8 data bits, no parity, 1 stop bit, no flow control.
- Access the CLI: Press Enter to get to the prompt. Type
enableto enter privileged EXEC mode. There is no default enable password on a factory-reset ASA. - Enter Global Configuration Mode: Type
configure terminal. - Configure Basic Settings:
- Set a hostname:
hostname ASA1. - Set an enable password:
enable secret <your_password>. - (Optional) Enable password encryption:
service password-encryption. - (Optional) Set the system clock and timezone for accurate logging.
- Set a hostname:
- Configure Management Interface IP (for ASDM access):
- Go to the interface configuration:
interface GigabitEthernet1/2(or the specific inside interface name). - Assign an IP address and subnet mask:
ip address 192.168.1.1 255.255.255.0(or your desired internal IP). - Assign a security level (e.g., 100 for inside network):
security-level 100. - Enable the interface:
no shutdown.
- Go to the interface configuration:
Phase 3: Launching ASDM (GUI Management)
- Connect PC to Inside Network: Connect your management computer to the same switch or network segment as the inside interface of the firewall.
- Set Static IP on PC: Assign a static IP address to your computer in the same subnet as the firewall’s inside interface (e.g., 192.168.1.10).
- Enable HTTP Server on ASA: In CLI global configuration mode, enable the HTTP server and allow access from your local network:
http server enable.http 192.168.1.0 255.255.255.0 inside(replace with your specific network info).
- Launch ASDM from Browser: Open a web browser on your PC and enter
https://<ASA_inside_IP_address>/admin(e.g.,https://192.168.1.1/admin). - Install/Run ASDM Launcher: Follow the on-screen instructions to download and install the Cisco ASDM Launcher application.
- Log In to ASDM: Open the ASDM Launcher, enter the firewall’s inside IP address, leave the username blank (unless you created one), and enter the enable password you set in the CLI.
Phase 4: Basic Configuration and Verification
- Use the Startup Wizard in ASDM to configure additional settings such as the outside interface IP address (static or DHCP from ISP), default route, and other basic parameters.
- Configure NAT: Set up Network Address Translation to allow internal hosts to access the internet.
- Define Access Rules/ACLs: Create Access Control Lists to control traffic flow between different security zones (e.g., allowing specific services from the outside to a DMZ server).
- Install Licenses: Obtain and install any necessary licenses (e.g., FirePOWER, VPN) from the Cisco licensing portal.
- Save Configuration: In CLI, type
write memoryto save the running configuration to permanent memory. - Test Connectivity: Verify internal hosts can access the internet and that defined access rules are working as intended by monitoring logs and testing traffic flow.
If you’re setting up a device like Fortinet, SonicWall, or pfSense, follow these simple steps:
Step 1: Physical Setup
- Place the firewall between your modem (internet source) and router.
- Connect power and turn it on.
Step 2: Access Settings
- Plug your PC into the firewall with an Ethernet cable.
- Open a browser and go to
192.168.1.1(or the IP in the manual). - Log in with the default username and password (then change the password right away).
Step 3: Initial Setup
- Run the setup wizard.
- Configure:
- WAN (Internet) – where you get your connection.
- LAN (Local Network) – your internal devices.
- Set time zone and admin password.
Step 4: Create Rules
- Go to Firewall Rules section.
Step 5: Turn On Logging
- Enable logs and email alerts so you know if someone tries to hack in
Installing pfSense – Best Choice for Businesses and Advanced Users
pfSense is one of the most popular and powerful open-source firewalls. Here’s a detailed but simple 4-step guide:
Step 1: Download & Prepare
- Get pfSense from pfsense.org/download.
- Create a bootable USB using Rufus or balenaEtcher.
Step 2: Install
- Boot your PC or appliance from the USB.
- Follow the on-screen steps to install pfSense on the system.
Step 3: Access Dashboard
- On another computer, go to
192.168.1.1in a browser. - Log in (default: admin / pfsense) and change password immediately.
Step 4: Configure & Protect
- Use the wizard to set the Internet (WAN) and the internal network (LAN).
- Add firewall rules (block everything first, then allow what you need).
- Enable logging and intrusion prevention to stop cyberattacks.
Step 5: Monitor & Maintain
Regularly monitor the dashboard for any unusual activity or alerts.
Update pfSense regularly to ensure the latest security patches are installed. Backup your configuration settings regularly to prevent any data loss in case of a system failure. By following these steps, you can effectively configure and protect your network using pfSense.
Best Practices in Firewalls
- Block first, allow later:Deny all traffic, then whitelist what you actually need.
- Use strong passwords: Never keep default ones.
- Keep firmware updated: New updates fix security holes.
- Turn on Intrusion Detection (IDS/IPS): Stops hackers automatically.
- Check logs often: Look for strange activity.
- Test with ShieldsUP: Visit grc.com/shieldsup to see which ports are open.
- Use a VPN: Don’t expose the admin panel to the open internet.
Common Mistakes to Avoid
- Forgetting to change default passwords.
- Leaving unnecessary ports open.
- Not turning on logging.
- Ignoring firmware updates.
Securing your data isn’t a one-time task. Keep updating, monitoring, and testing your firewall regularly for the best protection.
Installing and configuring a firewall may seem daunting, but with the right guide, it becomes an easy task. Whether you’re setting up a basic software firewall on your laptop or deploying an enterprise-grade hardware firewall, the steps outlined above will help you secure your digital environment.
Remember, cybersecurity is not a one-time fix. It requires regular updates, monitoring, and a proactive mindset.
Whether you are activating Windows Firewall on your personal laptop or setting up a more advanced solution like pfSense for your business, the ultimate objective remains to guard your network from potential cyber threats. It’s crucial to understand that cybersecurity is an ongoing process rather than a one-time event. Regularly updating, monitoring, and testing your firewall is essential for maintaining optimal protection. While the thought of installing and configuring a firewall may appear challenging, following a comprehensive guide can simplify the process significantly. By adhering to the steps provided above, you can effectively fortify your digital landscape against malicious attacks.
Citations
- Microsoft: https://support.microsoft.com
- Cisco: https://www.cisco.com
- pfSense: https://www.pfsense.org
- FTC: https://consumer.ftc.gov
- GRC ShieldsUP: https://www.grc.com/shieldsup
install a firewall, configure a firewall, firewall setup, how to install a firewall, pfSense firewall setup, Windows firewall configuration, firewall best practices, network security, firewall rules, software firewall, hardware firewall.
Leave a Reply